These days by default a user called root would be created on every Linux system. In distros like RHEL, fedora, CentOS during installation itself, you would be asked to create the default root account. The default ssh configuration allows all users to login to your server remotely. If a hacker try to brute force your root user password, then he would gain access to your system completely ! So for security reason, it’s not a good idea to have enabled remote login to root user. In this tutorial we would see how to disable remote login for root user on a Linux server.
There are two config files “ssh_config” and “sshd_config” under /etc/ssh/ directory. ssh_config file contains configuration pertaining to outbound SSH connections. where as sshd_config file contains configuration parameters which controls inbound SSH connections to the server itself.
Note : It’s always a good idea to backup important system files before you modify.
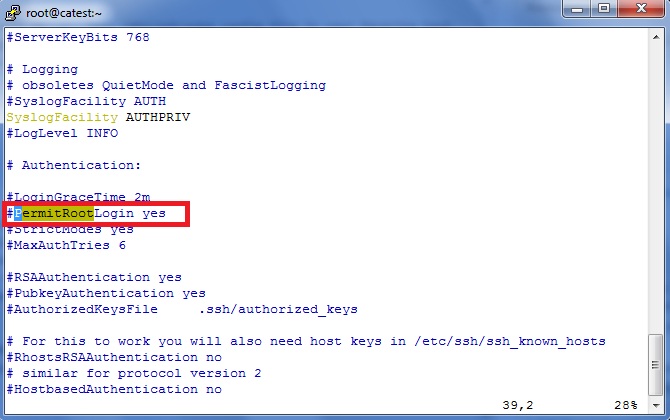
First we shall block root login from remote server. Open /etc/ssh/sshd_config file in your favorite text editor and find the line labeled PermitRootLogin. It will most likely be commented out using the # symbol as shown in the below image :
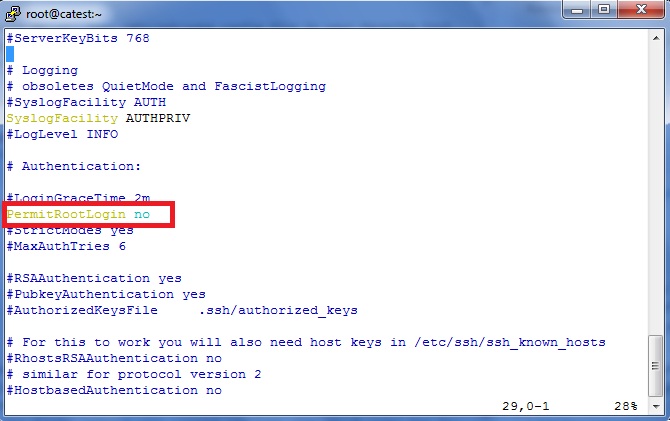
Remove the # symbol to make the line active, and then change “yes” to “no” as shown in the below image :
After modification, do not forget to restart the sshd service as shown below :
[root@catest ~]# service sshd restart
or
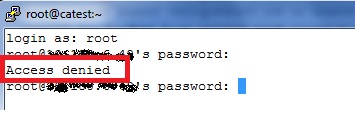
[root@catest ~]# /etc/init.d/sshd restartNow if you try to login from a remote server to your machine, you would be prompted with the below error :
To re-enable remote login for root user, comment (Add # symbol to the start of the line) the below line in /etc/ssh/sshd_config using your favorite editor :
#PermitRootLogin no
After modification, do not forget to restart the sshd service as shown below :
[root@catest ~]# service sshd restart
or
[root@catest ~]# /etc/init.d/sshd restartNow if you try to login from a remote server to your machine, you would be allowed to login !

