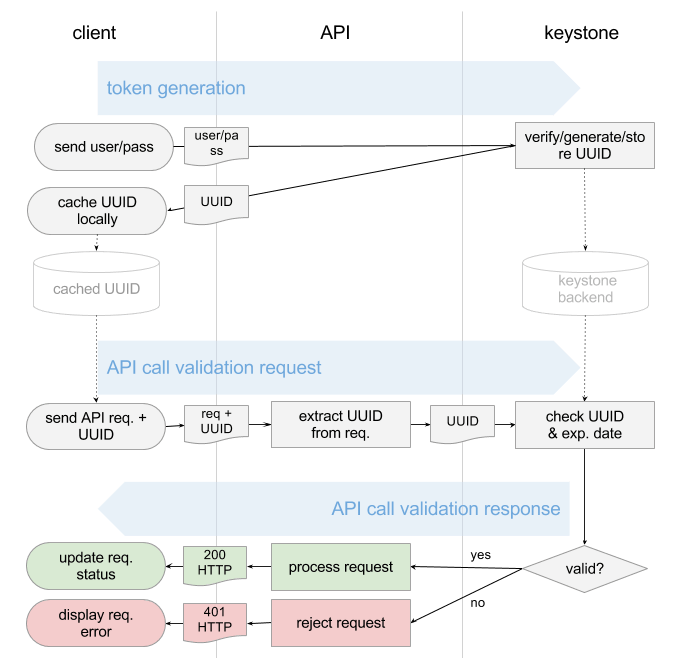
To access Openstack services through REST APIs, the identity service provides tokens. Clients can obtain the token by supplying their valid credentials to the Keystone authentication service. Credentials are usually a combination of username, password, and optionally the project ID. Once the token is obtained, we can connect to other OpenStack services such as Nova, Cinder, etc., using the token and their API endpoints. These tokens are temporary and short-lived (default 1-hour); which means it is safer to use than username/password pairs. Before we see how to generate OpenStack token using cURL, let us see the diagram below showing how tokens are generated by Keystone and then used by the client to “sign” every subsequent API request.
Below are the steps:
- The client sends username and password
- Keystone would:
- Generate a token.
- Store the token in its backend.
- Send a copy of the token back to the client.
- The client would cache the token.
- The token would be then passed along with each API call by the client.
- Upon each user request, the API endpoint would send this token back to Keystone for validation.
- Keystone would take the token and match it against its auth backend (check token string, expiration date).
- Keystone would return a “success” or “failure” message to the API endpoint.
- The further endpoint would process the request based on the Keystone return message.
For the demonstration purpose, we shall use cURL to obtain tokens:
The Identity endpoint: http://192.168.30.10:5000/v3/auth/tokens
Credentials to authenticate contain the below parameters:
- User Domain (required)
- Username (required)
- Password (required)
- Project Domain (optional)
- Project Name (optional)
- Project ID (optional)
Additionally, you can request the scope of a token based on Project and Domain. Below cURL command passes User Domain, Username, and Password along with the scope of the token to be project-based.
$ export TOKEN=`curl --silent -X POST -H "Content-Type: application/json" -d '{ "auth": { "identity": { "methods": ["password"], "password": { "user": { "name": "admin", "domain": { "id": "default" }, "password": "Openstack123" } } }, "scope": { "project": { "name": "admin", "domain": { "id": "default" } } } } }' -i "http://192.168.30.10:5000/v3/auth/tokens" | grep X-Subject-Token | cut -d ":" -f 2`
$ echo $TOKEN
gAAAAA...5R-dbCLGBlH-bH7rBIBjh84QhyQtRgqjO-VLvpneBXr....7P9QEach time you make a REST API request to an OpenStack service, you need to supply an authentication token in the X-Auth-Token request header. We shall see how to connect to Openstack services through API in a series of posts.
Read more about OpenStack API documentation here.