Shellshock vulnerability was found during the late 2014 (to be precise, the impact was posted on CVE-2014-6271 on 24 September 2014). Later an update was released in bash version 4.1.2-15 with a fix for Shellshock vulnerability. Well, the entire world gone on to update the bash and secured their shell from Shellshock, but surprisingly many machines in my office were not updated for whatever reasons. The scary part is, few of those machines with vulnerable shell were hosting many services in the internet. According to various blogs in the internet, Shellshock exploit allows an attacker to remotely execute a malicious command in bash via CGI scripts.
(I know this tutorial is pretty late, but there are many who are not aware of it and still using vulnerable bash on their public servers)
The first thing is to check if your BASH is Shellshock vulnerable or not. So any bash version prior to 4.1.2 is sure to have this vulnerability.
$ bash --version GNU bash, version 3.2.25(1)-release (x86_64-redhat-linux-gnu)
(or)
$ rpm -qa|grep bash bash-completion-1.3-7.el5 bash-3.2-32.el5_9.1
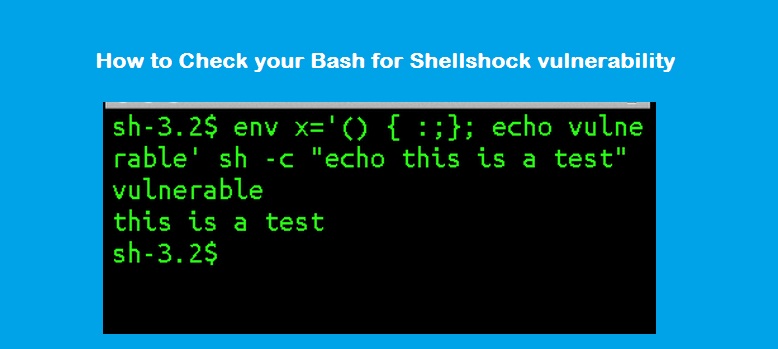
Now you know the version, so execute the below commands to confirm it’s vulnerable to Shellshock.
$ env x='() { :;}; echo vulnerable' bash -c "echo If you see the word vulnerable above, you are vulnerable to shellshock"
vulnerable
If you see the word vulnerable above, you are vulnerable to shellshockSolution:
Jump to the bottom of this post. In case, if you wish to know how shellshock works, then read through.
Understanding the export variables in SHELL :
As the above output says, your SHELL is vulnerable, but let’s see how it works.
Normally, you can set an environment variable and use it in a shell. For example, as below:
$ test=1 $ echo $test 1
But you can’t directly use the env variable ‘test’ in a new bash shell. Check it out:
$ test=1 $ echo $test 1 $ bash $ echo $test
Output is blank. The reason is, an environment variable is available for access only in the same shell. But if you export an environment variable, then it’s available for a new bash shell as well. Here’s an example:
$ var="testing" $ export var $ bash $ echo $var testing
Now you can see variable ‘$var’ was set and exported in one shell and accessed from another shell. Of course, you can stop export anytime using the below command.
$ export -n var $ bash $ echo $var
Similarly, you can create functions and export it in one shell and access the exported function from another shell. Let us see that example as well.
$ fnc() { echo "testing"; }
$ fnc
testing
$ bash
$ fnc
bash: fnc: command not foundIn the above output you see ‘bash: fnc: command not found‘ because, the fnc is not an exported function. So you cannot call it from another shell.
Let’s export ‘fnc‘ as well.
$ export -f fnc $ fnc testing $ bash $ fnc testing
It works as expected (since ‘fnc‘ was exported and it’s available in another shell).
Exporting a variable or a function will set an environment variable
$ env | grep -A1 fnc
fnc=() { echo "testing"
}Now Shellshock exploit
Based on the above examples, we learnt that a new bash shell ingests the definition of an environment variable starting with () and interprets it as a function. But vulnerability here’s, the new shell will execute whatever present in the quote.
For example:
Execute the below command:
$ export sse_fnc='() { echo "function shellshock exploit" ; }; echo "Not good"; 'Check env variable for ‘sse_fnc’:
$ env | grep -A1 sse_fnc
sse_fnc=() { echo "function shellshock exploit" ; }; echo "Not good";Go to new bash shell:
$ bash Not good
Note: We just typed ‘bash‘ and you see the text ‘Not good‘ printed. It means, the new shell starts to execute the function after reading the environment variable and executes the trailing commands as well (even though the function brace closed after the ‘echo “function shellshock exploit” ;’).
In other words “The exported variable sse_fnc was passed to the subshell which was interpreted as a function sse_fnc but the trailing commands were executed (this is bad) as the subshell spawned.”
via Fixee@StackExchange
how this vulnerability can be exploited?
I don’t think anyone can explain better than this guy (shellshocker.net). Thanks man!
How to Fix Shellshock?
Simple, update your bash and try the exploit to check whether the vulnerability has gone away.
$curl https://shellshocker.net/fixbash | sh
The above command will automatically download around 30+ patches and compile bash from source. You can regularly run this script to keep your bash updated with latest patches.
Once the installation is successful. Check bash version as below:
$bash --version GNU bash, version 4.3.42(1)-release (x86_64-unknown-linux-gnu)
Test Shellshock vulnerability:
$env x='() { :;}; echo vulnerable' bash -c "echo If you see the word vulnerable above, you are vulnerable to shellshock
If you see the word vulnerable above, you are vulnerable to shellshockFrom the above output, it didn’t print “vulnerable’ word. So my bash is secure!
(or)
$env X='() { (shellshocker.net)=>\' bash -c "echo date"; cat echo; rm ./echoIf BASH is vulnerable, the above command will output date. Else, BASH is secure.