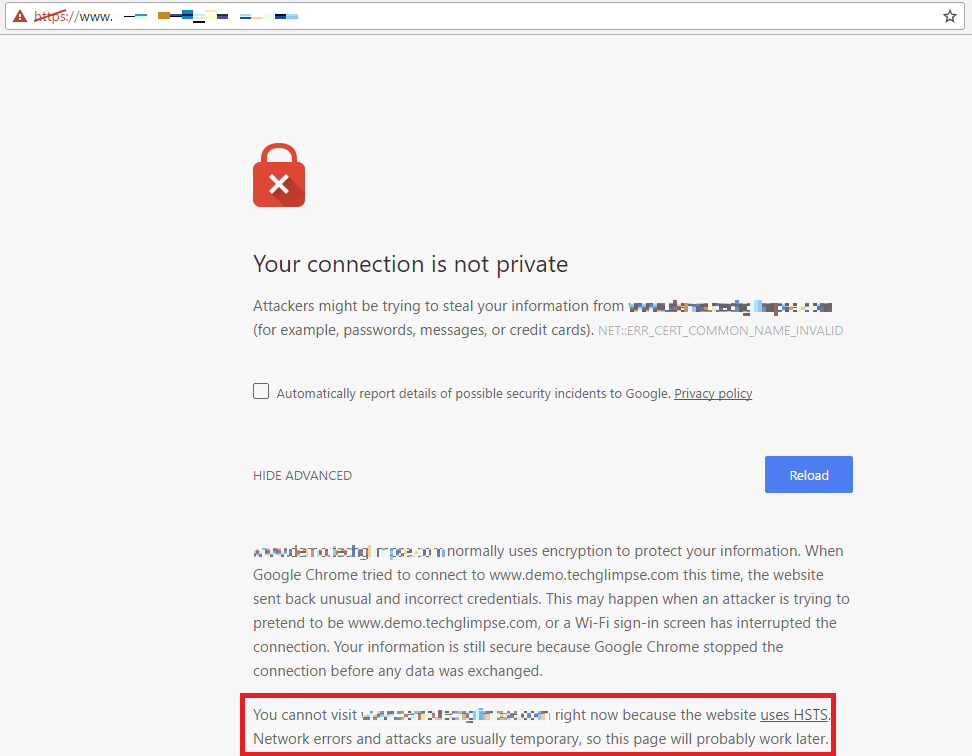
Once I had enabled HSTS (HTTP Strict Transport Security) for my https website powered by Cloudflare. But later on due to performance issue, I had to disable Cloudflare, so that the website is served directly from my VPS running Apache web server. I had also turned off HSTS in Apache web server. The issue here is – when I access the website now, the browser throws an error message “Your connection is not private” and there was a detailed error message under Advanced which states as below:
“You cannot visit www.example.com right now because the website uses HSTS. Network errors and attacks are usually temporary, so this page will probably work later.”
It took a while for me to understand the reason for this error. Before I speak about that, have a look at the screen shot of the error.
To understand the issue, let’s consider two scenarios:
- When HSTS enforced by the Web server
- When HSTS not enforced by the Web server (say, you decided to turn off HSTS)
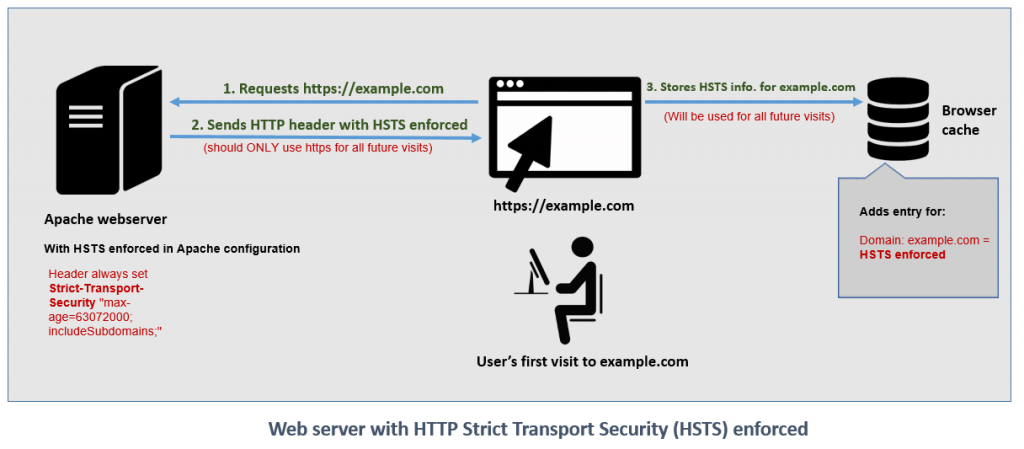
Scenario 1: When HSTS enforced by the Web server:
In this scenario, my website was served via Cloudflare (where the HSTS was enforced with an expiration period)
- The user visits the site over secured channel (https)
- The server sends a HTTP header: Strict-Transport-Security (HSTS) along with the content to the user’s web browser.
- The browser displays the content and stores HSTS enforced information in its cache and it will be used for all future visits. The duration of the HSTS information stored in the cache depends on the server settings. For e.g., if the server enforced HSTS with an expiration time as 6 months, then the data in the user’s browser cache will be valid only for 6 months. It means, the browser expects the website to always enforce HSTS until 6 months. After 6 months, if the browser loads the same website again it will update the cache with the current value.
The below image explains the above scenario:
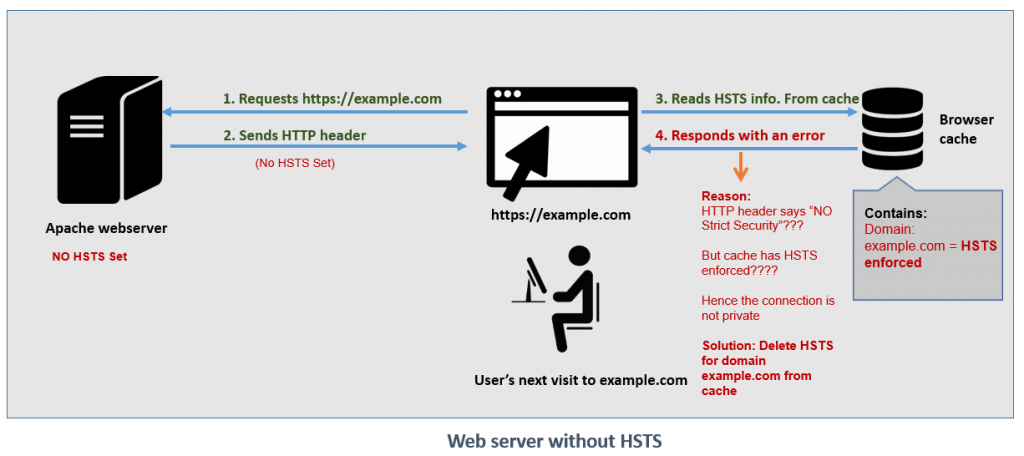
Scenario 2: When HSTS not enforced by the Webserver (say, you decided to turn off HSTS)
In this scenario, my website has been moved out of Cloudflare and hosted on my own server running Apache HTTP (where HSTS was not enforced)
- The next time when user visits the site over secured channel (https)
- The server will send a HTTP header (without HSTS enforcement) to the user’s browser.
- The browser reads the cache information related to HSTS and understands that it has HSTS enabled and that contradicts with the HTTP header sent by the web server.
- Hence, browser thinks “Attacker is trying to pretend to be example.com” and denies the access to the page.
The below image explains the second scenario:
And that’s the reason Chrome and Firefox browsers refused to load the website. It means, I have to delete the HSTS information for my domain from the browser cache. Below are the steps to do that in Google Chrome.
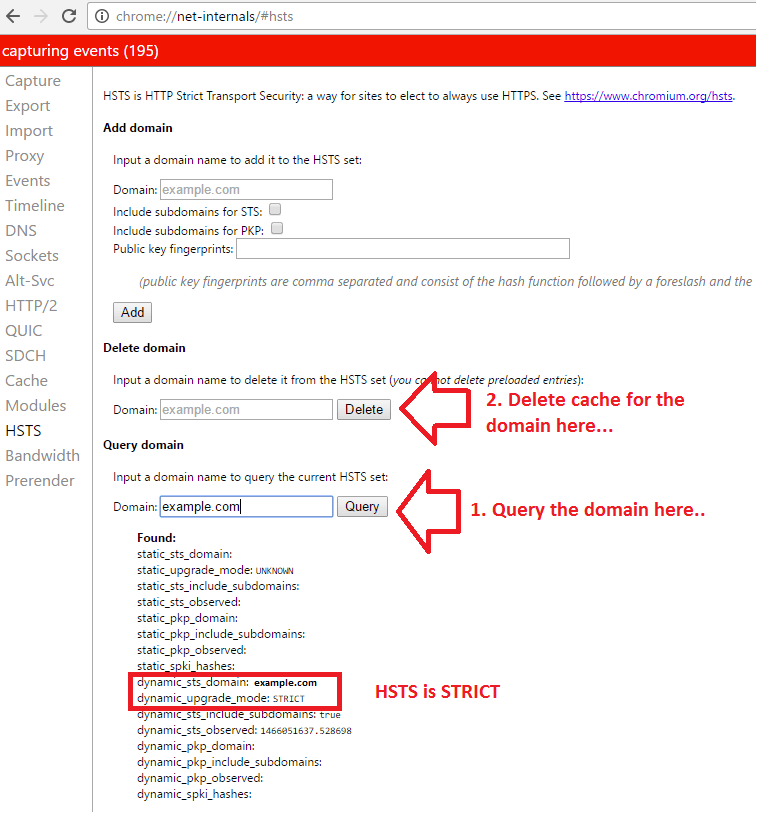
How to delete HSTS Cache from Chrome browser?
Step 1: Go to chrome://net-internals/#hsts
Step 2: Search domain under “Query domain” and lookout for the information from the cache.
Step 3: To clear the cache of a domain, you need to delete the domain under “Delete domain” heading.
Step 4: That’s it! You can now load the website to see if it works. Now the browser will obtain new HTTP header information and update its cache.
HSTS is a good security feature, but if you decide to disable it for some reason, then you might land up with an issue. Hope it helps someone out there.


please update
it didn’t work
Thanks but it didn’t work at all.
Doesn’t work
It did not work for me I still have same error
having problems with all https site. including google.com. you cant delete this one