Have you enabled DNSSEC on DNS Server? If not, learn how to enable DNSSEC on Bind based DNS Server. Once you have installed and configured DNSSEC validating secure DNS server, make sure you test it properly. As an administrator, here are the basic testing that you should do after setting up DNSSEC enabled DNS Server. Ensure that the DNS domains that are DNSSEC signed are validated correctly by reporting Authenticated Data (AD) flag and the DNS domains with broken DNSSEC are not validated with SERVFAIL. However, the resolver should resolve non-DNSSEC domains as normally. We’ll see how to validate DNSSEC using both the command and web service.
How to validate DNSSEC signed domains using dig?
dig @<dnsserver> <dnssec-signed-domain> +dnssec +multi
Lets test a DNSSEC signed domain now!
$ dig dnssectest.sidn.nl +dnssec +multi
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @10.180.8.1 dnssectest.sidn.nl +dnssec +multi
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 44295
;; flags: qr rd ra ad; QUERY: 1, ANSWER: 4, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 4096
;; QUESTION SECTION:
;dnssectest.sidn.nl. IN A
;; ANSWER SECTION:
dnssectest.sidn.nl. 21600 IN CNAME www.sidn.nl.
dnssectest.sidn.nl. 21600 IN RRSIG CNAME 8 3 86400 20131214071501 (
20131114071501 42033 sidn.nl.
oN/P1jg9Zcx4+2XK+dZXw4OhlsGJAEK14kcIv4VQsxM0
CZoyvwGsd23CpfY3k1tPXBDOy/oE+gjO0FDq+5eXXERt
lTA+5Mu9tjnM5TDW66IFgOgtRN5Hw79BjAHpIR06igjX
O+hk9ZqKOWCMVjyJvDgRB3PbkRIe6PNmjmgA5Y8= )
www.sidn.nl. 10466 IN A 213.136.31.220
www.sidn.nl. 10466 IN RRSIG A 8 3 86400 20131213071501 (
20131113071501 42033 sidn.nl.
QKN3pfWJ5S0i97zRtczt1wSUQhKAO3rFfxxZs/JY/hK4
p6QXTQO6znVJ2niut644CO2IT5pBYhgNjYlsbUxh1WJs
Qdyxkf5YgOwlRY/MD6rqMaF45LFHy6JurCXTPL+t593d
9WZDr5DmXrVIsm0VClo0W/beIkEsHfE6j/Yeq1Y= )
;; Query time: 1610 msec
;; SERVER: 10.180.8.115#53(10.180.8.115)
;; WHEN: Thu Nov 14 16:43:14 2013
;; MSG SIZE rcvd: 415In the above output, look out for Authenticated Data (AD) set in FLAGS. Requesting DNSSEC signed DNS domain with the DO Flag set (which is DNSSEC OK) should provide an Authenticated answer (AD) flag set in the header.
Validating broken or misconfigured DNSSEC domain
$ dig dnssec-or-not.org +dnssec +multi
; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @10.180.8.1 dnssec-or-not.org +dnssec +multi
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 23634
;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags: do; udp: 4096
;; QUESTION SECTION:
;dnssec-or-not.org. IN A
;; Query time: 334 msec
;; SERVER: 10.180.8.115#53(10.180.8.115)
;; WHEN: Thu Nov 14 16:46:32 2013
;; MSG SIZE rcvd: 46Trying to resolve a domain which has DNSSEC issues should return SERVFAIL as return code in the header. Lookout for SERVFAIL from the above output.
Validating non-DNSSEC signed domain, should resolve Normally
$ dig espncricinfo.com +dnssec +multi ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> @10.180.8.1 espncricinfo.com +dnssec +multi ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 46851 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags: do; udp: 4096 ;; QUESTION SECTION: ;espncricinfo.com. IN A ;; ANSWER SECTION: espncricinfo.com. 102 IN A 80.168.92.141 ;; Query time: 431 msec ;; SERVER: 10.180.8.115#53(10.180.8.115) ;; WHEN: Thu Nov 14 16:51:12 2013 ;; MSG SIZE rcvd: 61
Trying to resolve a domain that is not DNSSEC signed, should resolve normally. Why espncricinfo.com? Well, I was watching Sachin Tendulkar’s Last and 200th Test match against West Indies. What a legend!
Few Web Services for DNSSEC Testing
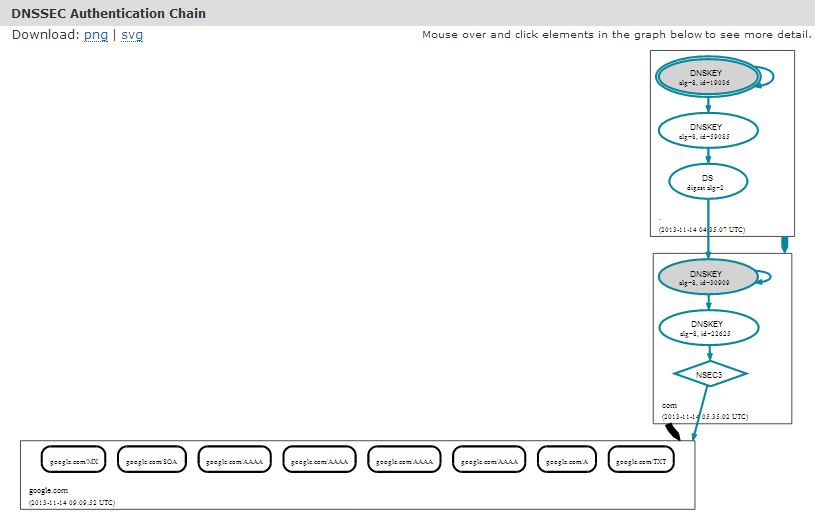
DNSVIZ
It’s a web service to visualize the status of a DNS zone. It helps you to understand and troubleshoot the DNSSEC deployment issues by providing visual analysis of the DNSSEC authentication chain and its resolving path. The tool is capable of listing the configuration errors during the validation process.
Checkout DNSVIZ.
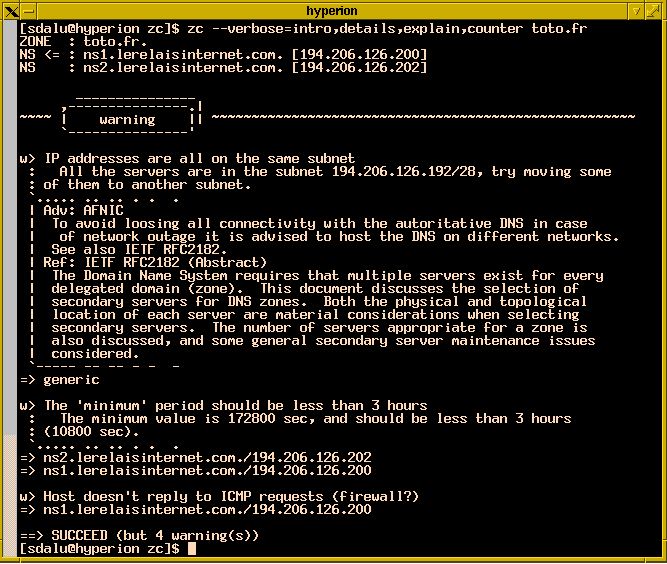
ZoneCheck
ZoneCheck is a simple tool that allows you to find out and solve DNS misconfigurations. It checks zone for incorrect configurations or inconsistencies (due to latency of the application) and generates a report.
Verisign’s SecSpider
SecSpider monitors deployment metrics of DNSSEC, Availability metrics, Verifiability metrics, Validation metrics etc…
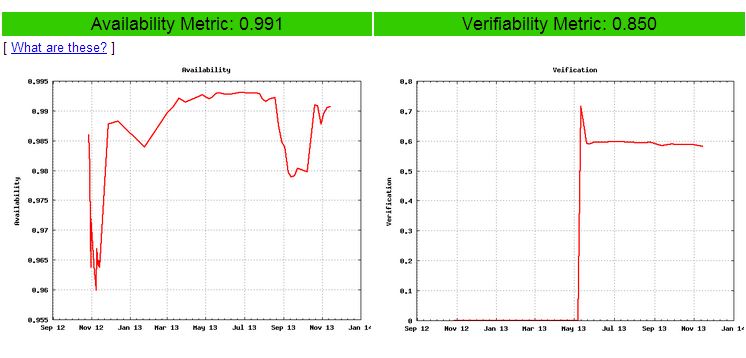
Check SecSpider.
And more…
* Verisign Labs developed “DNSSEC or not?” validator. Checkout here.
* SIDN developed “Are you a protected DNSSEC?” – Checkout here.
* ICSI Netalyzer, a network testing tool, which includes DNSSEC validation as well – Checkout here.
* A Similar one from University Duesseldorf, Germany – Checkout here.