If an attacker gains root login to your system, he can do more damage than if he gains normal user login. We have seen from our previous article – How to disable remote login for root user on Linux machine. Now we shall see after all if we have some 10 user accounts created on a Linux server(for different group activities like HR, Finance etc.,), we no need to allow remote login to all of those 10 accounts. In this tutorial, we shall see how to allow or deny specific user accounts to do remote login to Linux server.
SSH provides 4 following directives to allow or deny to access the server. By default it allows all groups and Users.
- AllowGroups
- AllowUsers
- DenyGroups
- DenyUsers
Note: Before modifying any system level configuration, please do take necessary backup.
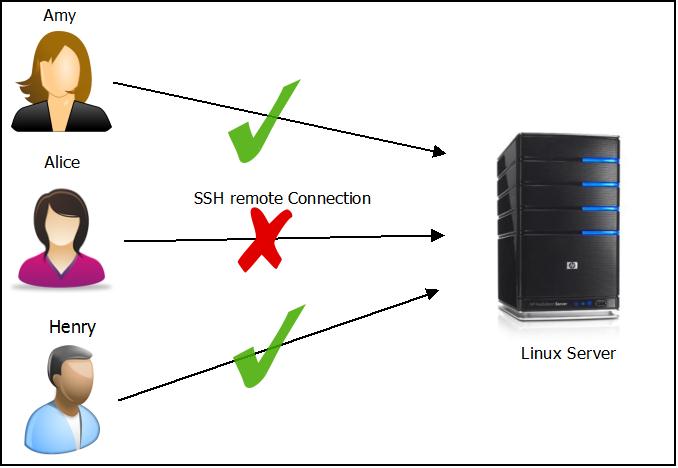
To allow specific two users called Amy and henry remotely login to the server add the below lines into /etc/ssh/sshd_config file using your favorite editor (VIM is my favorite editor).
AllowUsers admin amy
Further to control easily for the future, you can add multiple users onto a single group and allow the user based on the group they belong to. For eg: consider henry and amy are working together in finance department. Create a common group name called finance as shown below :
groupadd –r finance
Now create both the users henry and amy belonging to finance group as shown below :
useradd -G finance henry
useradd -G finance amy
To allow users who belong to specific group called finance to remotely login to the server add the below line into /etc/ssh/sshd_config file.
AllowGroups finance
With this we no need to use AllowUsers.
The other alternatives directives are DenyGroups and DenyUsers which perform the exact opposite of the aforementioned AllowGroups and AllowUsers respectively.
To verify the proper update of configuration file, without restarting the sshd service run the below commands :
[root@catest ~]# /usr/sbin/sshd -t [root@catest ~]# echo $? 0 [root@catest ~]#
If the echo $? command outputs 0 then the verification is successful, else you will see an error stating what the erroneous data is :
[root@catest ~]# /usr/sbin/sshd -t /etc/ssh/sshd_config: line 116: Bad configuration option: AllowUser /etc/ssh/sshd_config: terminating, 1 bad configuration options [root@catest ~]#
After verification do not forget to restart sshd as shown below :
[root@catest ~]# /etc/init.d/sshd restart

