TRUST is the word that comes to our mind when we speak about Certificate Authority. StartSSL, a certificate authority that provides free SSL certificate with a validity of one year for non-commercial use. An initiative that aimed to secure the internet traffic has now lost TRUST – StartSSL distrusted! The CA lost trust well during October 2016 – below is the statement from Mozilla. Lookout for the update below regarding the termination of StartCom’s SSL service.
Mozilla has discovered that a Certificate Authority (CA) called WoSign has had a number of technical and management failures. Most seriously, we discovered they were backdating SSL certificates in order to get around the deadline that CAs stop issuing SHA-1 SSL certificates by January 1, 2016. Additionally, Mozilla discovered that WoSign had acquired full ownership of another CA called StartCom and failed to disclose this, as required by Mozilla policy.
Also, the statement from Google.
Google has determined that two CAs, WoSign and StartCom, have not maintained the high standards expected of CAs and will no longer be trusted by Google Chrome
I have a SSL Certificate issued by StartSSL, will this affect my website?
The answer is YES and NO.
Yes, if your certificate was issued after October 21, 2016 00:00:00 UTC. Because they are not trusted by the browsers.
No, if your certificate was issued before October 21, 2016 00:00:00 UTC. The browsers may continue to trust as long as they comply with browser policy. But that’s risky, because you never know when the browsers will stop trusting those as well.
Certificate issued by StartSSL is about to expire and renewing it will solve the issue?
No! In fact, this site was using a certificate that was issued by StartSSL and it was due for renewal. And the moment I tried to renew it, this is what StartSSL said.
StartSSL CA was distrusted during October 2016 and six months from then is April 2017. So I expected the company to have made necessary changes to comply with CA policies and reconsideration has been requested to Google, Mozilla and Apple. But sadly, that was not the case. I renewed and installed the new certificate to only see security warning by the browser.
StartSSL certificates will be trusted again?
Hopefully after few months. But its been six months since it was distrusted and certificates issued even after 6 months are not trusted by the browsers. Have they submitted the request to Google, Mozilla & Apple for reconsideration? Even the official website of StartSSL does not say when the authority will be trusted again, but they are still selling certificates. However, for now, using StartSSL is not advised.
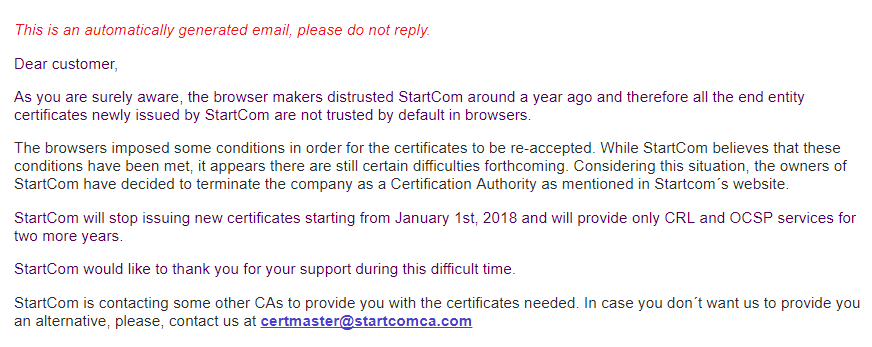
Update 02-Dec-2017: StartCom’s StartSSL service has been terminated! Below is the mail from StartCom regarding their service termination.
So, what’s the alternative?
Alternatives for StartSSL
a) You may buy a commercial certificate from a trusted certificate providers.
(or)
b) Choose another free Certificate Provider – like LetsEncrypt.
How to secure your Website using LetsEncrypt?
LetsEncrypt is a free, automated and open Certificate Authority that provides SSL certificate with a validity of 90 days.
Installing LetsEncrypt certificate is pretty simple. All you need to do is, use Certbot – a script that automatically requests certificate from LetsEncrypt and enables HTTPS on your website. Certbot supports Apache, Ngnix and Haproxy.
Step 1: Download Certbot
# wget https://dl.eff.org/certbot-auto
Step 2: Set execute permission
# chmod a+x certbot-auto
Step 3: Checkout the various options supported by the script.
# ./certbot-auto -h
The script supports plugin for web servers as shown below:
--apache Use the Apache plugin for authentication & installation --standalone Run a standalone webserver for authentication --nginx Use the Nginx plugin for authentication & installation --webroot Place files in a server's webroot folder for authentication --manual Obtain certs interactively, or using shell script hooks
By default, the script will obtain and install certificate in your current web server. In case, if you just need to obtain certificate and don’t want to install it in the web server, then use certonly option as shown below:
# ./certbot-auto --apache certonly
Testing and Dry-run: The below options can be used to request a test certificate and perform a dry-run to test certificate renewals.
--test-cert Obtain a test cert from a staging server --dry-run Test "renew" or "certonly" without saving any certs to disk
Certbot does not support multiple Virtual Hosts in single configuration file
The certbot script needs all of your domains to be configured in a separate Virtual Hosts configuration file. For instance, I had setup VirtualHosts for all of my domains (including the primary domain and sub domains) in httpd.conf file – a single file containing multiple vhosts. In this case, the certbot script was able to obtain certificate for all the domains, but couldn’t authenticate itself to install in the web server. According to this thread, the behavior was intentional to avoid errors while installing certificates. So if you have multiple virtual hosts configured in a single file, then you need to split it across different virtual hosts file before executing certbot-auto command.
Obtain certificate from LetsEncrypt and Install
# ./certbot-auto Obtaining a new certificate Performing the following challenges: tls-sni-01 challenge for domaina.com tls-sni-01 challenge for sub.domainb.com Waiting for verification... Cleaning up challenges Generating key (2048 bits): /etc/letsencrypt/keys/0000_key-certbot.pem Creating CSR: /etc/letsencrypt/csr/0000_csr-certbot.pem Deploying Certificate for domaina.com to VirtualHost /etc/httpd/conf.d/domaina-com.conf Deploying Certificate for domainb.com to VirtualHost /etc/httpd/conf.d/domainb-com.conf
Where are the certificates stored?
All the live certificates will be stored under /etc/letsencrypt/live/. Also checkout other directories under /etc/letsencrypt.
[letsencrypt] # ls accounts archive csr keys live options-ssl-apache.conf renewal
What is the validity of Certificates issued by LetsEncrypt?
Use openssl command to verify the certificate validity as shown below:
# openssl x509 -startdate -enddate -in /etc/letsencrypt/live/domaina.com/cert.pem notBefore=May 4 09:29:00 2017 GMT notAfter=Aug 2 09:29:00 2017 GMT
Renew Certificates
Since the certificate issued by Let’s Encrypt will expire in 90 days, you need to renew the certificate automatically before they expire. The ‘renew‘ option will allow you to renew the certificates and –dry-run option will help you to simulate renewal process.
$./certbot-auto renew
Simulate certificate renewal:
$./certbot-auto renew --dry-run ------------------------------------------------------------------------------- Processing /etc/letsencrypt/renewal/domaina.com.conf ------------------------------------------------------------------------------- Cert not due for renewal, but simulating renewal for dry run Renewing an existing certificate Performing the following challenges: tls-sni-01 challenge for domaina.com Waiting for verification... Cleaning up challenges Generating key (2048 bits), not saving to file Creating CSR: not saving to file ------------------------------------------------------------------------------- new certificate deployed with reload of apache server; fullchain is /etc/letsencrypt/live/domaina.com/fullchain.pem ------------------------------------------------------------------------------- ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates below have not been saved.) Congratulations, all renewals succeeded. The following certs have been renewed: /etc/letsencrypt/live/domaina.com/fullchain.pem (success) ** DRY RUN: simulating 'certbot renew' close to cert expiry ** (The test certificates above have not been saved.) IMPORTANT NOTES: - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal.
Setup Cron job for automatic certificate renewal
# crontab -e
And add the below lines:
0 0 * * * /usr/bin/certbot-auto renew 30 13 * * * /usr/bin/certbot-auto renew
Note: Remember to set the correct path to certbot-auto script and ensure cron is run twice a day. Well, the certbot-auto will do nothing unless the certificate is due for renewal.