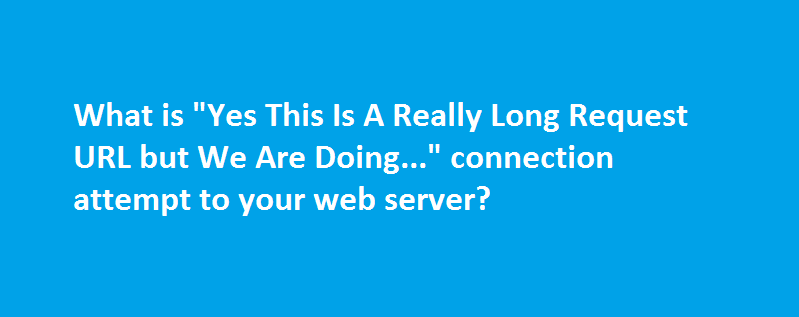
Today, I noticed a strange connection attempt to my server requesting for a long file name – that starts as ‘/YesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurpose……………….’. Below is the snapshot from the Apache error log.
[Thu May 11 17:52:01 2017] [error] [client 137.226.113.7] (36)File name too long : access to /YesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURL butWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserA gentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForRes earchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeA reDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTH XYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoin gItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurpose PleaseHaveALookAtTheUserAgentTHXYesThisIsAReallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScanningForResearchPurposePleaseHaveALookAtTheUserAgentTHXYesThisIsAR eallyLongRequestURLbutWeAreDoingItOnPurposeWeAreScann failed.
Understood? Here’s the version with space between the words:
Yes This Is A Really Long Request URL but We Are Doing It On Purpose. We Are Scanning For Research Purpose. Please Have A Look At The UserAgent. THX
As hinted in the above message, I looked into the Apache access_log.
137.226.113.7 HTTP/1.1" 403 1202 "-" "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/46.0.2490.86 Safari/537.36 Scanning for research (researchscan.comsys.rwth-aachen.de)"
The above snapshot shows that the traffic was sent from researchscan.comsys.rwth-aachen.de – the website talks about a research project at RWTH Aachen University located at Germany. The quick lookup of IP address 137.226.113.7 reveals that the machine is located within the university’s network.
The research website explains why such connection attempts are made and why are they collecting such data. The data collected through these connections are expected to help scientists study the deployment and configuration of network protocols and security technologies.
So if you notice such connection attempts to your web server, then this particular connection attempt seems to be harmless and you can be less bothered about it. However, if you wish to exclude your server from this connection, then you may contact the research team in this address ‘researchscan@comsys.rwth-aachen.de’ with your IP address or CIDR block. Alternatively, set your firewall to drop packets from the subnet (137.226.113.0/26) that is scanning your server.
Though this connection request is not a malicious attempt, you should be securing your website or application from malicious attacks. Carry out Vulnerability Assessment and Penetration Testing before launching any application or website.