Enabling Two step authentication for WordPress admin is one of the most important step in securing your website. By default, WordPress provides login based authentication and authorization method, which might be vulnerable to brute-force attacks!
In this guide, I’ll demonstrate how to enable two step authentication for WordPress admin pages, which provides an additional level of authentication, making the brute-force attacks much difficult.
Password protect wp-login.php
Password protecting /wp-admin/ itself can break some of the WordPress functionalities and plugins as they use AJAX. Still with bypassing authentication for AJAX we can protect /wp-admin/, but then the developers of WordPress suggest that protecting wp-login.php with password is just sufficient.
Create password file: .htpasswd
Basically, it’s a simple authentication mechanism. We shall have the username and encrypted passwords in a simple text file. When the user enters the username and password, the web server encrypts the entered password and matches with the .htpasswd file. There are different methods to create the password file.
Create the password file using Apache Utilities
Many hosts provide tools to create the password file. You can use htpasswd command, shipped by httpd-tools package.
[root@ra ~]# htpasswd -c .htpasswd david New password: Re-type new password: Adding password for user david
The above command would generate the password file as shown below:
[root@ra ~]# more .htpasswd david:$apr1$YiymNG1K$54e10fkFfLV3.zKbF6puJ1
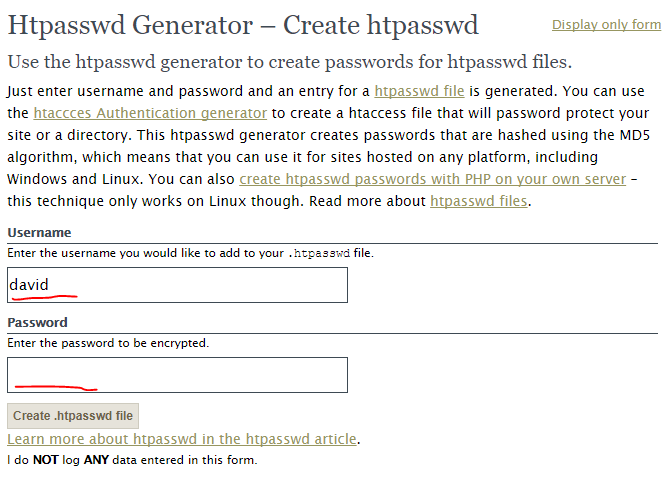
Generate the Password file online
You can also use an online htpasswd generator. Enter the username and password:
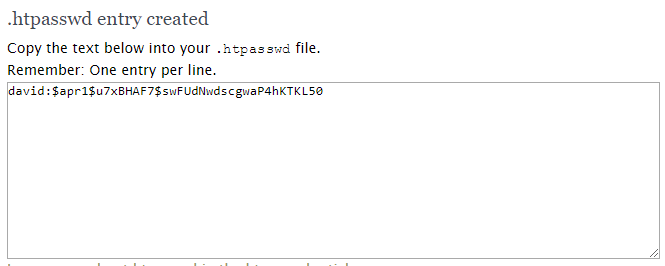
Once done, press Create .htpasswd file button. Then copy the text into .htpasswd file.
Create the password file using OpenSSL utilities
This is for an advanced user. If you have OpenSSL installed on your server, then you can create the password file with no additional packages. Don’t have OpenSSL installed? Here’s a tutorial to help you in installing OpenSSL.
Let’s first add a username onto the file using the below command:
$ sh -c "echo -n 'david:' >> .htpasswd"Next add an encrypted password for the above username using the below command. Enter the passwords when prompted.
$ sh -c "openssl passwd -apr1 >> .htpasswd" Password: Verifying - Password:
$ more .htpasswd david:$apr1$YiymNG1K$54e10fkFfLV3.zKbF6puJ1 sammy:$apr1$8UEfCuC/$bVMZTG5meMINvm3qrVo.k. samm:$apr1$9Oc5Lytr$6hC51eLMqiS4y7S8hPAze1
Enable Two step Authentication for WordPress Admin in Nginx
In Nginx, the password protection is provided by HttpAuthBasicModule. Once you have created the password file (.htpasswd), you need to add directives to Nginx’s site configuration file within your domain server block as shown below:
location ^~ /wp-login.php {
auth_basic "Restricted";
auth_basic_user_file /etc/nginx/passwd;
## PHP Handler
fastcgi_pass unix:/var/run/php-fpm/php-fpm.sock;
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME $document_root$fastcgi_script_name;
fastcgi_param SCRIPT_NAME $fastcgi_script_name;
include fastcgi_params;
}Using auth_basic and auth_basic_user_file you are protecting the wp-login.php, but upon successful authentication, to process the PHP files you need to add the PHP Handler too.
Once you update, test your changes:
# nginx -t
Upon successful, reload the Nginx to apply the new configuration
On CentOS 6.x and below
# service nginx reload
On CentOS 7.x and above
# systemctl reload nginx
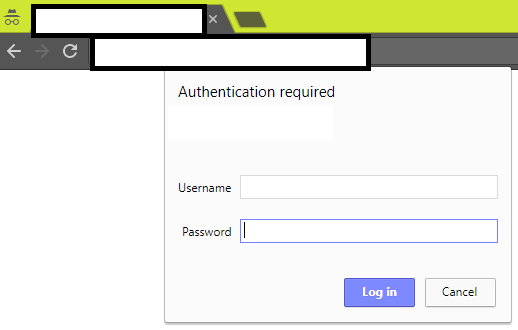
Now navigate to wp-login.php or wp-admin file in the browser to see an additional protection as shown below:
Enable Two step Authentication for WordPress Admin in Apache
Unlike Nginx, here you can configure either in Apache configuration file or just configure in .htaccess file.
Configure Password Protect to wp-login.php within .htaccess
Insert the below code in .htaccess file located in the WordPress directory.
<Files wp-login.php>
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /etc/httpd/.htpasswd
require user <username>
</Files>
Don’t forget to update the .htpasswd file location and the username in the above code.
Configure Password Protect to wp-login.php in Virtual Host
Open your domain virtual host configuration file and insert the below contents in red:
<VirtualHost *:80>
ServerAdmin webmaster@localhost
DocumentRoot /var/www/html
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
<Directory "/var/www/html">
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
<Files wp-login.php>
AuthType Basic
AuthName "Restricted Content"
AuthUserFile /var/www/html/wordpress/.htpasswd
require user david
</Files>
</VirtualHost>Don’t forget to update the .htpasswd file location and the username in the above code.
Once you update, test your changes:
# apachectl configtest Syntax OK
Upon successful, reload the httpd to apply the new configuration
On CentOS 6.x and below
# service httpd reload
On CentOS 7.x and above
# systemctl reload httpd
Now navigate to wp-login.php or wp-admin file in the browser to see a prompt requesting for username & password.