Today, I was alerted by Wordfence plugin about a malicious file on my client’s website. The messages said “File appears to be malicious: functio
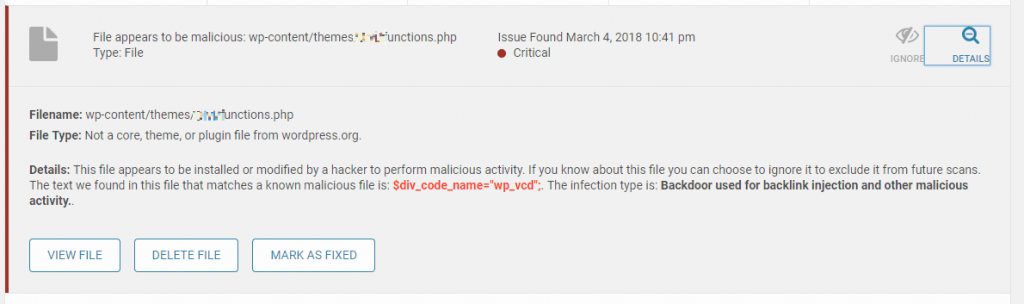
Below is the screenshot of the Wordfence report.
The report says that the theme’s functions.php file has been injected with a malicious code $div_code_name="wp_vcd" and the injection type is a possible backdoor. So what’s this wp-vcd malware and how to clean it? Well, this tutorial will explain the same.
What’s WP-VCD malware?
Just google it and you will understand that the wp-vcd is one of the popular malware that affects WordPress websites. The malware aims to inject spams ads or links into the infected website.
What are the various forms of WP-VCD malware?
Though the aim of the malware is to inject spams ads and links into the infected website, it’s appears to be in different forms.
- According to the post from Medium, some of the affected sites contained a malicious file called
'wp-vcd.php'insidewp-includesfolder and the same was included inwp-includes/post.phpandfunctions.phpfiles.
<?php if (file_exists(dirname(__FILE__) . '/wp-vcd.php')) include_once(dirname(__FILE__) . '/wp-vcd.php'); ?><?php [..Rest of File..]
- According to another report, there was no file named
wp-vcd.php, but instead the file named ‘class.theme-modules.php‘ was included in theme’sfunctions.phpfile.
<?php if (file_exists(dirname(__FILE__) . '/class.theme-modules.php')) include_once(dirname(__FILE__) . '/class.theme-modules.php'); ?>- In my client’s website, there was no file named
wp-vcd.phporclass.theme-modules.php, instead I found a piece of code written inside theme’sfunctions.phpfile.
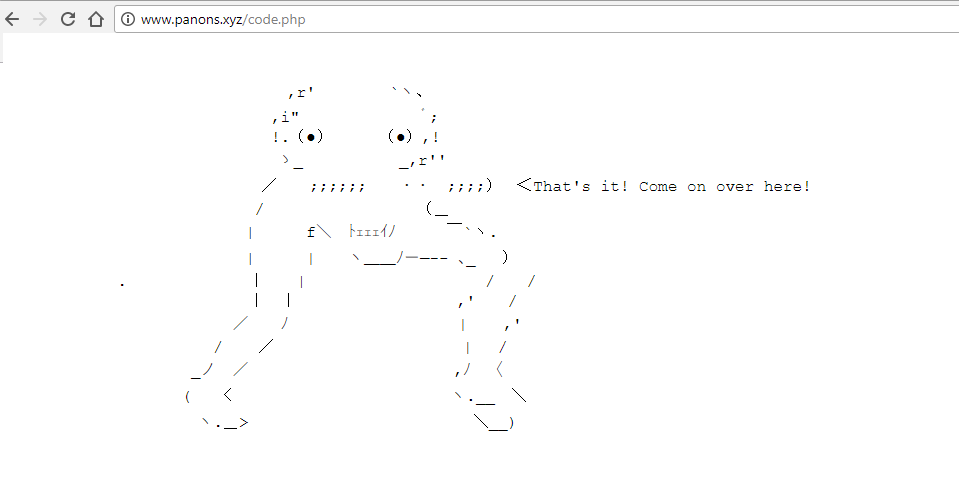
The code seems to download a content from a malicious website (see the below screenshot) with varied top-level domains such as .xyz, .com,.cc, .me etc…Though .com, .cc & .me domains didn’t load, .xyz just displayed a strange creature with a message “That’s it! Come on over here! “. Have a look at the screenshot below.
Well, I did enough research to understand WP-VCD is malicious, now I want to get rid of those from my client’s website. How to do that? Here’s it is.
How to clean wp-vcd malware
Step 1: Scan your website using Wordfence plugin
Step 2: Read through the scan report and understand which are the files are infected.
Step 3: Login to your server or cPanel and backup the site and database. I know, those backups would contain malicious codes, but you have no option (unless you have clean backup)
Step 4: Remove all the infected files from the website. It could be wp-vcd.php or class.theme-modules.php or the malicious code inside theme’s functions.php file. You should also check if the WordPress core files are infected. To do that, you might want to replace the existing core files and plugins with the one downloaded from official WordPress repository.
Step 5: Scan the site again using Wordfence and ensure the site is clean.
Step 6: It’s not too late. Secure WordPress site now. Here are few guides to help you out.
- 50 things to do after installing WordPress
- WordPress Injected With Spam Links? Diagnose & Protect your site
- Deleted WordPress user account, but it appeared again! Seriously, it happened in my client’s website.
Step 7: Never ever use free premium themes. Most of the premium themes that are available for free download are hacked and might contain malicious codes.


Hi!
Thanks a lot for your post.
RC