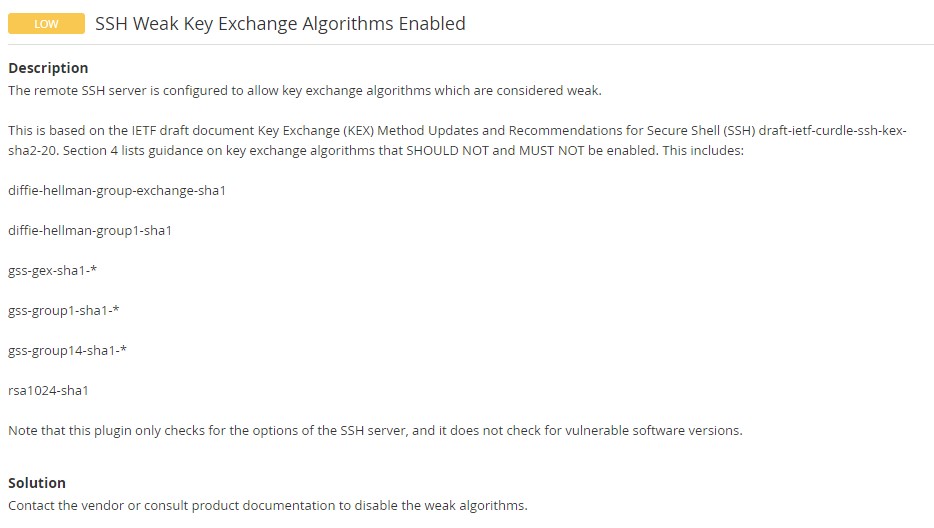
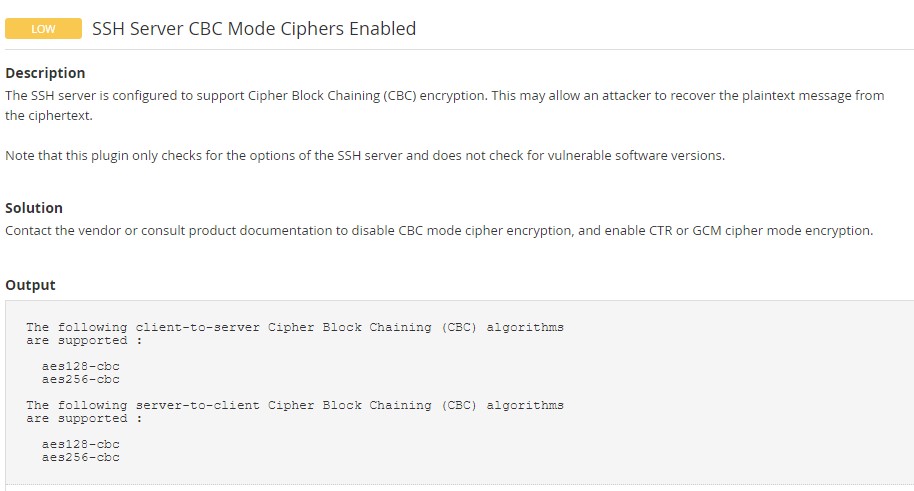
Nessus vulnerability scanner reported – SSH Weak Key Exchange Algorithms Enabled and SSH Server CBC Mode Ciphers Enabled. The detailed message suggested that the SSH server allows key exchange algorithms which are considered weak and support Cipher Block Chaining (CBC) encryption which may allow an attacker to recover the plaintext from the ciphertext. Well, this tutorial is all about how to disable weak key exchange algorithms and CBC encryption mode in the SSH server on CentOS Stream 8.
Below are the screenshots right from the Nessus report.
How to Disable Weak Key Exchange Algorithm and CBC Mode in SSH
Step 1: Edit /etc/sysconfig/sshd and uncomment the following line.
#CRYPTO_POLICY=
to
CRYPTO_POLICY=
By doing that, you are opting out of crypto policies set by the server. If you want to use the system-wide crypto policies, then you should comment CRYPTO_POLICY= and use update-crypto-policies command to enable/disable policies. Learn more about Crypto policies.
Step 2: Copy the following ciphers, MACs, and KexAlgorithms to /etc/ssh/sshd_config.
KexAlgorithms curve25519-sha256@libssh.org,ecdh-sha2-nistp521,ecdh-sha2-nistp384,ecdh-sha2-nistp256,diffie-hellman-group-exchange-sha256 Ciphers chacha20-poly1305@openssh.com,aes256-gcm@openssh.com,aes128-gcm@openssh.com,aes256-ctr,aes192-ctr,aes128-ctr MACs hmac-sha2-512-etm@openssh.com,hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512,hmac-sha2-256,umac-128@openssh.com
Step 3: Verify the configuration file before restarting the SSH server.
sshd -t
Step 4: If there are no errors reported, then restart the SSHD service.
# systemctl restart sshd
Step 5: Test weak CBC ciphers by executing the below command.
ssh -vv -oCiphers=3des-cbc,aes128-cbc,aes192-cbc,aes256-cbc [user@server-ip]
For example:
$ ssh -vv -oCiphers=3des-cbc,aes128-cbc,aes192-cbc,aes256-cbc centos@192.168.10.141 ::::::::::::::::::::::::::::::::::::::: debug2: KEX algorithms: curve25519-sha256,curve25519-sha256@libssh.org,ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512 debug2: host key algorithms: rsa-sha2-512,rsa-sha2-256,ecdsa-sha2-nistp256,ssh-ed25519 debug2: ciphers ctos: aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr debug2: ciphers stoc: aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr debug2: MACs ctos: hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-256,umac-128@openssh.com,hmac-sha2-512 debug2: MACs stoc: hmac-sha2-256-etm@openssh.com,umac-128-etm@openssh.com,hmac-sha2-512-etm@openssh.com,hmac-sha2-256,umac-128@openssh.com,hmac-sha2-512 debug2: compression ctos: none,zlib@openssh.com debug2: compression stoc: none,zlib@openssh.com debug2: languages ctos: debug2: languages stoc: debug2: first_kex_follows 0 debug2: reserved 0 debug1: kex: algorithm: curve25519-sha256 debug1: kex: host key algorithm: ecdsa-sha2-nistp256 Unable to negotiate with 192.168.10.141 port 22: no matching cipher found. Their offer: aes256-gcm@openssh.com,chacha20-poly1305@openssh.com,aes256-ctr
The above error means that the weak ciphers are disabled. In case, if you see the password prompt, then it means weak ciphers are enabled.


Thanks a lot guy
Thanks this article was helpful for me