For one of my project using OpenCA, i had to migrate from sha1 to sha2. Firstly i should find the underlying OpenSSL supports sha2? Here i share some of my findings and solutions. Openssl(version 0.9.7h and later) supports sha256, but by default it uses sha1 algorithm for signing. In this tutorial we shall see how to generate a digital x509 certificate with sha256 digest algorithm. “By the by did i tell you that sha1 is already broken!” Checkout the article sha1 broken.
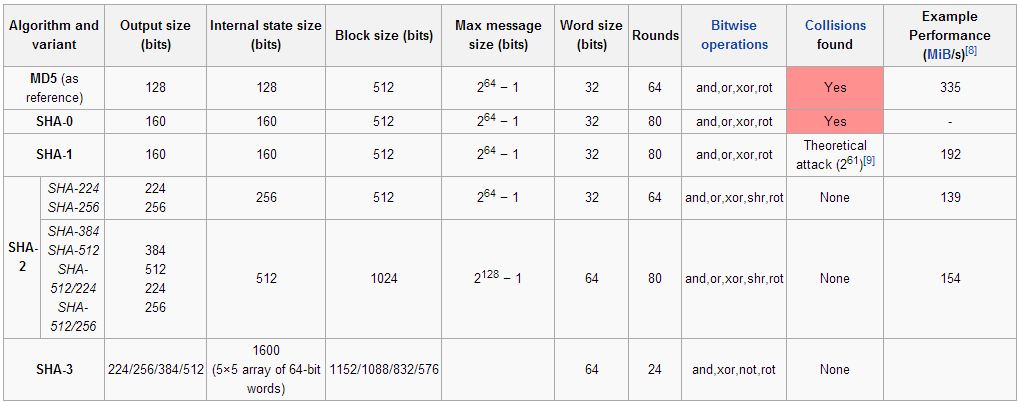
Below image gives you the comparison of SHA functions:
Before proceeding further, find out OpenSSL, an open source toolkit used to implement the Secure Socket Layer (SSL) and Transport Layer Security (TLS) protocols is installed? The toolkit is loaded with tons of functionalities that can be performed using various options. Learn about 20 most useful OpenSSL commands which would help us further understanding the generation of x509 sha256 hash self-signed certificate.
Prerequisites: You need to have OpenSSL installed to execute the commands mentioned in this tutorial. If you don’t have one, click here to install it.
Step 1: How to find openssl support for sha256
Run the below command to find out whether your openssl version supports sha256 digest :
#openssl dgst --help
Sample Output :
Fri Feb 07>$openssl dgst --help unknown option '--help' options are -c to output the digest with separating colons -d to output debug info -hex output as hex dump -binary output in binary form -sign file sign digest using private key in file -verify file verify a signature using public key in file -prverify file verify a signature using private key in file -keyform arg key file format (PEM or ENGINE) -signature file signature to verify -binary output in binary form -engine e use engine e, possibly a hardware device. -md5 to use the md5 message digest algorithm (default) -md4 to use the md4 message digest algorithm -md2 to use the md2 message digest algorithm -sha1 to use the sha1 message digest algorithm -sha to use the sha message digest algorithm -sha224 to use the sha224 message digest algorithm -sha256 to use the sha256 message digest algorithm -sha384 to use the sha384 message digest algorithm -sha512 to use the sha512 message digest algorithm -ripemd160 to use the ripemd160 message digest algorithm
Step 2: How to generate x509 SHA256 hash self-signed certificate using OpenSSL
sha256 is part of sha2 which consists of other hash functions like sha224, sha256, sha384, sha512 etc., in which sha256 and sha512 are the popular ones. Run the below OpenSSL command to generate a self-signed certificate with sha256 hash function. This certificate can be used as SSL certificate for securing your domain transactions.
#openssl req -x509 -nodes -sha256 -days 365 -newkey rsa:2048 -keyout techglimpse.com.key -out techglimpse.com.crt
Read More: How to encrypt your password using sha256 hashing algorithm.
Step 3: Verify sha256 hash function in self-signed x509 digital certificate
Now the certificate is generated, you need to verify whether the certificate is actually used sha256 hash function for encryption. Here is the OpenSSL command through which you can verify:
#openssl x509 -noout -text -in techglimpse.com.crt
This command will list all the information about the digital certificate such as validity, signature algorithm, Public key length etc., You can also verify a website’s SSL certificate is using SHA1 or SHA2 hash function using OpenSSL commands
Sample Output :
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
f4:49:d3:ec:cc:9a:4e:01
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=IN, ST=KA, L=BANGALORE, O=CDAC, CN=Test.com
Validity
Not Before: Feb 7 07:09:30 2014 GMT
Not After : Feb 7 07:09:30 2015 GMT
Subject: C=IN, ST=KA, L=BANGALORE, O=CDAC, CN=Test.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (2048 bit)
Modulus (2048 bit):
00:c1:bc:2c:71:25:73:89:9f:4a:c6:a2:03:b5:3d:
02:8d:bb:99:12:67:f0:51:fd:a1:b7:a2:26:a0:73:
19:de:f8:b1:06:f2:d6:55:44:bb:a3:8d:ef:8e:b3:
fa:18:a3:10:07:54:0a:be:a4:29:0d:62:fc:dc:e6:
bb:3c:e8:6d:6d:2e:fa:0a:b3:7c:8a:ec:f8:c5:57:
a6:51:02:3a:9b:9e:8a:66:0e:69:e5:ae:bc:c9:15:
05:e4:f0:14:b0:46:71:8a:b6:72:3c:9d:23:a0:e4:
1b:94:13:69:5a:5c:ab:dc:22:4a:54:93:01:2b:20:
b7:b4:b2:a7:5f:76:5e:b8:85:41:19:a6:47:ff:cb:
35:45:59:b3:fe:7d:b8:ff:ac:4b:32:0f:68:ca:88:
c4:8d:63:01:b3:01:94:32:79:e7:2f:e9:6e:21:d3:
f2:28:ef:c3:2f:f7:e0:47:51:d1:61:0e:78:52:60:
d5:bc:1d:98:98:54:0b:51:dd:28:f4:7a:a5:a0:cd:
b3:1c:da:80:95:65:e7:32:91:df:61:de:cd:5c:d2:
74:e5:de:e1:24:3d:e7:29:23:d2:28:00:85:ce:d6:
11:1a:25:68:c7:f1:8f:dd:82:dc:01:43:a5:0b:c4:
e7:90:f8:8e:f0:ab:37:ed:32:44:7c:89:4b:c0:a7:
dc:7f
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
EF:12:34:E0:D9:A8:82:C5:C0:E5:28:71:4A:EC:6B:CD:43:60:95:70
X509v3 Authority Key Identifier:
keyid:EF:12:34:E0:D9:A8:82:C5:C0:E5:28:71:4A:EC:6B:CD:43:60:95:70
DirName:/C=IN/ST=KA/L=BANGALORE/O=CDAC/CN=Test.com
serial:F4:49:D3:EC:CC:9A:4E:01X509v3 Basic Constraints:
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
b2:d4:22:79:73:56:22:6e:3e:8c:4f:0d:44:ad:d9:a8:46:2b:
9c:4b:c1:ee:b3:ec:a5:58:95:15:49:9e:2a:88:6a:5f:79:31:
af:28:0d:21:da:50:d8:42:77:07:8c:b7:4c:ef:e6:7d:49:7f:
17:69:66:27:a3:ef:cb:a6:72:ef:eb:7c:95:29:3f:03:3c:f9:
74:2a:9e:66:88:2a:91:39:63:0b:9c:39:21:b1:83:3f:44:d3:
4b:c3:d7:d0:d9:bc:b0:8f:79:e1:66:29:03:52:5c:0c:af:a9:
0f:3b:4f:4d:ad:44:aa:be:6d:99:9b:9f:53:b5:89:e6:14:5b:
92:b1:ef:9b:39:9b:ba:e5:d3:f8:4a:c4:a7:74:43:59:7e:1a:
6a:2b:74:ef:10:85:0f:ec:65:2c:57:b8:5c:bc:36:a5:78:84:
2c:11:b1:e4:b5:3c:1d:b9:06:17:7e:d3:09:1c:58:af:de:1d:
3f:b4:1c:a8:1b:d5:53:34:e8:fd:bc:28:39:b7:05:5b:85:9b:
8e:e7:13:ac:52:83:20:93:25:b3:68:57:34:09:c0:89:2c:05:
25:e3:3c:11:6e:09:f9:90:d4:84:e0:ea:77:fc:fe:af:79:38:
f0:65:97:d2:77:fb:00:76:88:8e:df:e1:cc:30:33:dd:01:77:
e4:c2:c8:cc
Checkout the below video:
Also Read : OpenSSL Commands you must know.
Enjoy! If you have any issues, please feel free to post a comment and I’ll try my best to answer it!