If you were surfing the internet recently, you would have noticed many websites write about “Heartbleed” with the image of a bleeding heart. If you thought this is some medicine related science, you are totally wrong. Heartbleed is a serious security vulnerability found in the most popular OpenSSL cryptographic software library used by many of the websites to encrypt data. Lets see in brief about OpenSSL and the new Heartbleed security issue.
What is OpenSSL?
OpenSSL is an open-source implementation of Secure Sockets Layer (SSL), and Transport Layer Security (TLS) protocols that are widely used for enabling secure transactions online. It is estimated that more than 66% of services on the web use OpenSSL. And for a long time since, we have thought that the SSL/TLS were so very secure, and these were the codes that were the partners of the secret handshake that took place behind every transaction and was behind most of the URLs that started with https://.
OpenSSL works fine now too, but there is a hole discovered, that gives anyone a chance to read through the information sent through the secret handshake. And you would be surprised to know that the hole was not created now, but it existed for years. Be happy that the hole is now found and named “Heartbleed”!
What is Heartbleed?
Heartbleed is actually not a problem with SSL/TLS, but a coding mistake. A single code that allows the attackers to read huge amount of data and steal information. Researchers have said,
Without using any privileged information or credentials we were able steal from ourselves the secret keys used for our X.509 certificates, user names and passwords, instant messages, emails and business critical documents and communication.
And if you are highly technical, and interested much to know how this bug aroused and how it can be fixed, here is an informative article from Gizmodo, Q&A from Heartbleed website.
What Websites and Services Are Affected by Heartbleed?
Many websites that are running versions of OpenSSL (1.0.1 and 1.0.2-beta ,1.0.1f and 1.0.2-beta1) are found to be affected with this bug. Rejoice, that many websites which run on the older versions and websites that have upgraded already to the fixed version are safe.
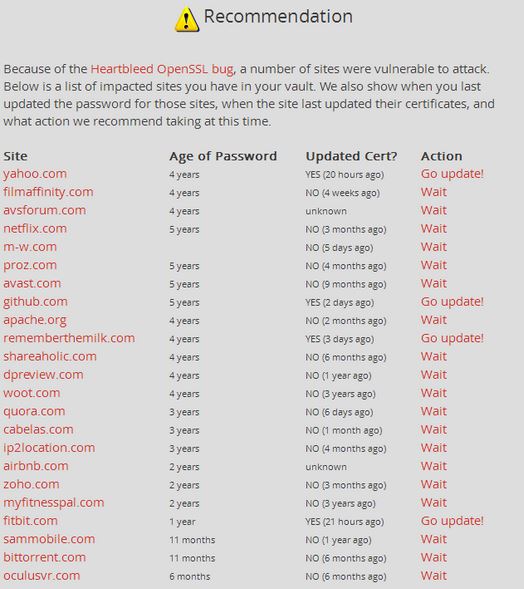
Checkout the list of possibly affected sites here. You can test the vulnerability of specific sites using the tool by LastPass. This tool gives a snapshot of the last-time when the sites SSL certificate was regenerated. But if you wanted to know about the recent updates of a website and their steps taken to overcome the Heartbleed bug, be sure to check their respective blogs.
What can you do? Change your account passwords in all websites?
In this case of the Heatbleed bug, there is not much you can really do. This problem is only completely solvable by the service owners. And it can be fixed, if they upgrade OpenSSL to a bug fixed version.
What you can do is, only if possible, try to avoid using the vulnerable website until they issue a fix and notify you. Because changing the password in a vulnerable website, does not help you at any stage!
But you need to keep in mind that your favorite website may have been vulnerable sometime in the past two years time. If your provider, has upgraded to the fixed version of OpenSSL, make sure you change your account passwords. Since the Heartbleed not only allows the attacker to get the current information, but also the past data.
If a site is not affected, its safe to update your passwords. At-least it can be a precautionary action!