In our previous article, we had shared with you all the security concerns of using the now popular video conferencing application Zoom. Ever since the allegations about said concerns were raised, Zoom has come into action trying to make the platform more and more secure, from announcing a 90-days long break to any feature update and focusing on upgrading security, to introducing measures like Waiting Room to give the host more control on who can get into a meeting as an added layer of cross-checking the participant list.
This article contains a compilation of measures that you can take to make your meetings relatively more secure. However, this still doesn’t mean that the application is secure for your meetings if they’re professional and contain valuable or confidential information you’re always encouraged to try out the alternatives that provide better security, but more on that in our next article.
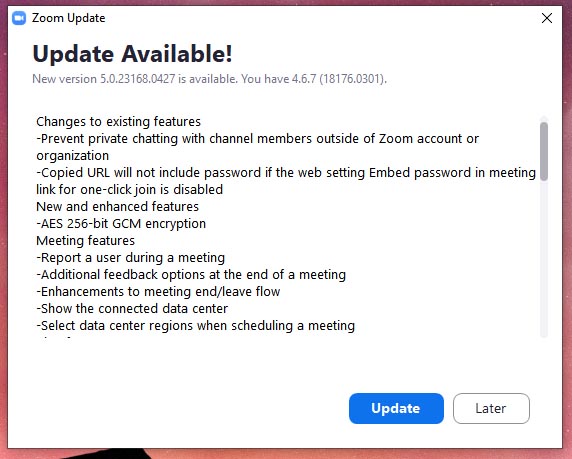
As for the server-side of things, Zoom is reportedly working on the betterment of their end to end encryption and other security measures that were found to have issues previously, to ensure the privacy of its now 300 million+ user base. For starters, they’re now implementing the AES 256-bit GCM or Galois/Counter Mode encryption, which provides near equal focus towards both security and performance of the application, system-wide with the rollout of Zoom version 5.
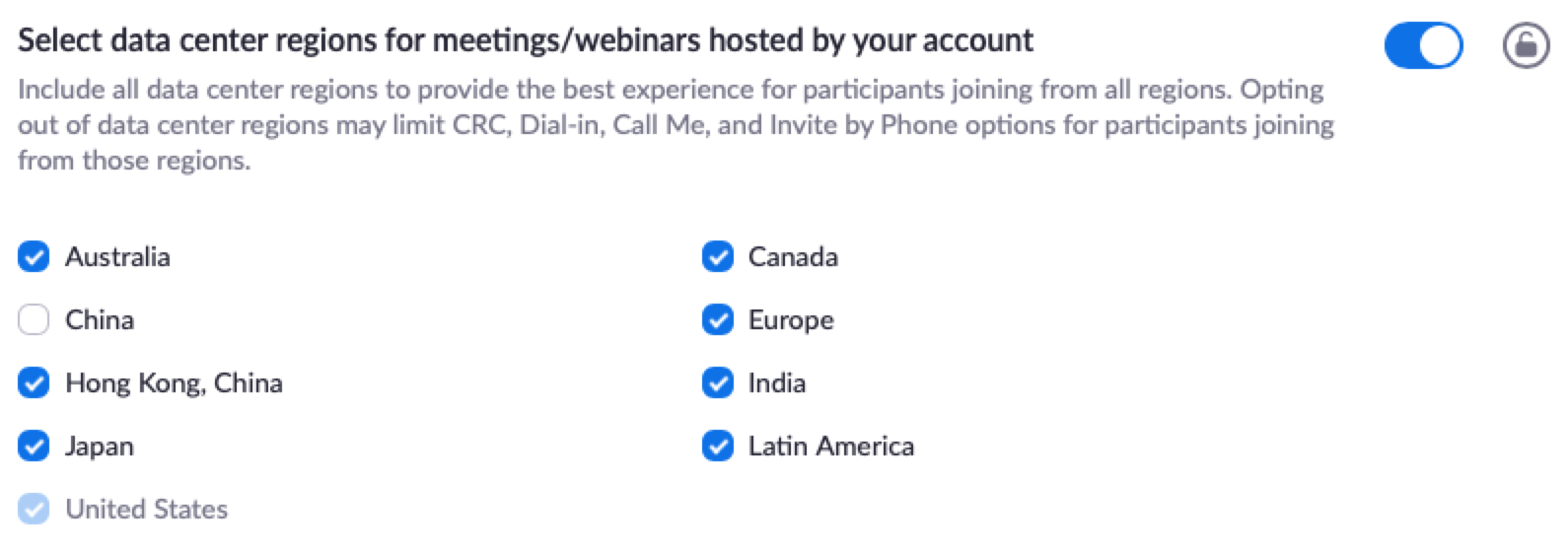
Zoom is also adding an option for the admin to select the region of data centers through which their data is routed in case they wish to avoid any. Administrators now also get to report ZoomBombers.
Here’s how you can get started with your side of enabling secure settings on the Zoom website:
How to Secure Zoom meetings
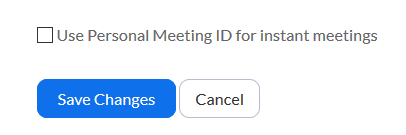
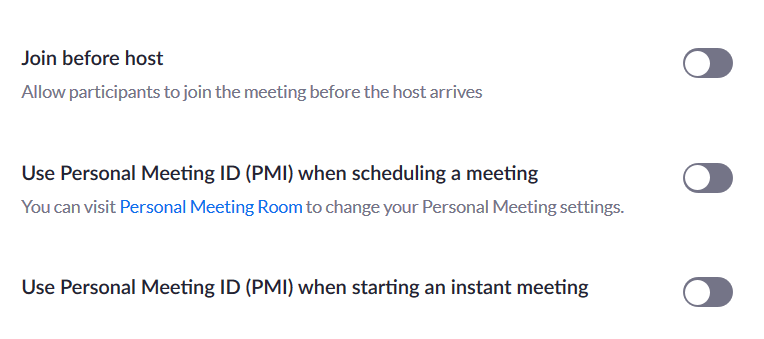
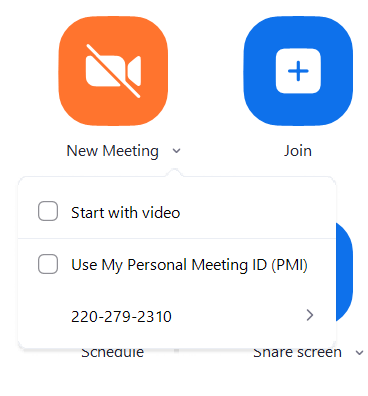
Don’t use Personal Meeting ID for instant meetings
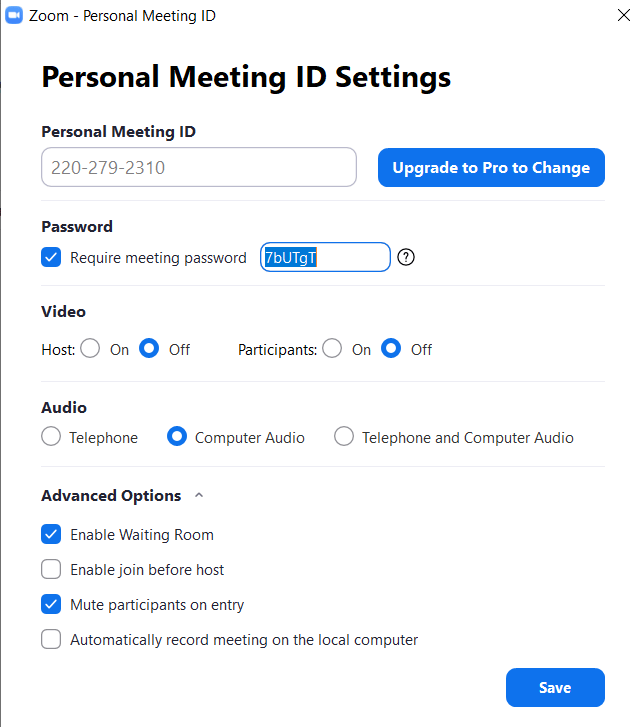
Zoom assigns a unique personal meeting id to each user and this ID cannot be customized unless you upgrade to the paid version. In order to secure your identity, it’s advisable to not use this id for your meetings. Uncheck the Use Personal Meeting ID for instant meetings and now, you will be given a randomly generated ID for each of your meetings.
Navigate to the settings section and make sure your PMI is not being used for any purpose.
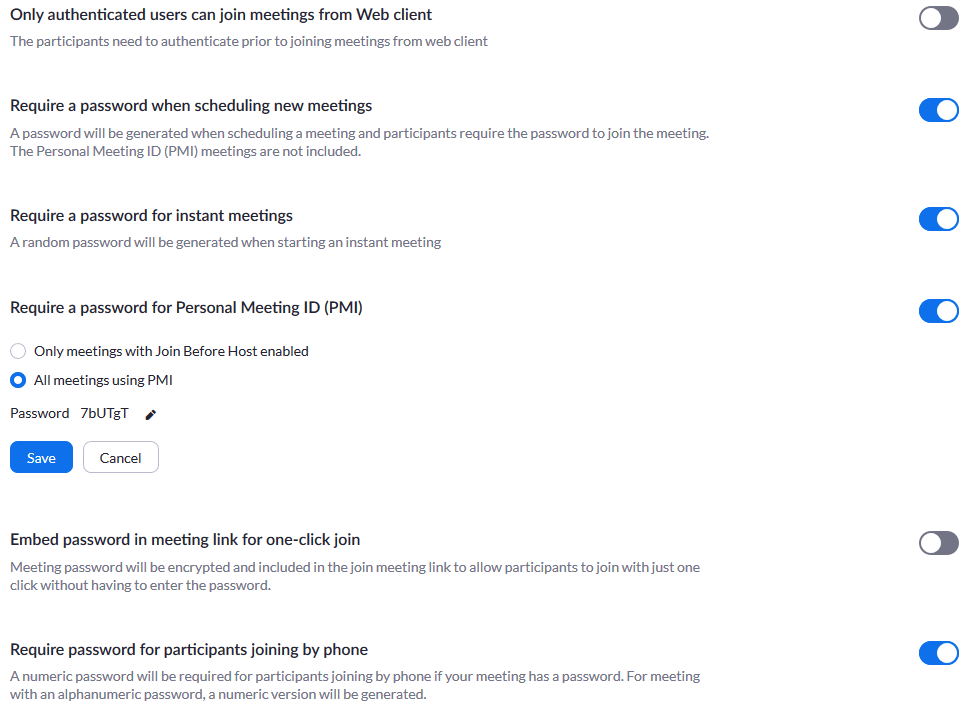
Authenticate users joining the meeting
If you are hosting a meeting, authenticate the users joining your meeting, thereby not letting random strangers join your meeting. You can also set a password for your meetings for extra security.
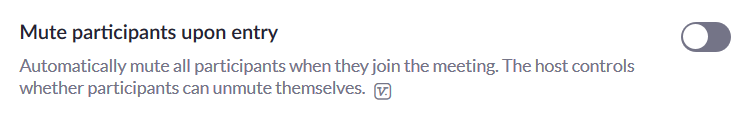
Mute participants to avoid disturbances
Mute the participants once you start the meeting to avoid unwanted disturbances.
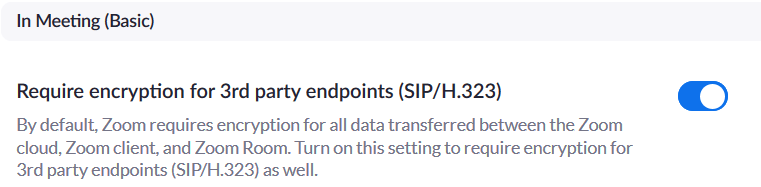
Enable new GCM encryption
This setting enables the new GCM encryption regardless of the client-side endpoints using SIP or H.323 protocols to ensure that the connectivity stays secure regardless of other variables at play.
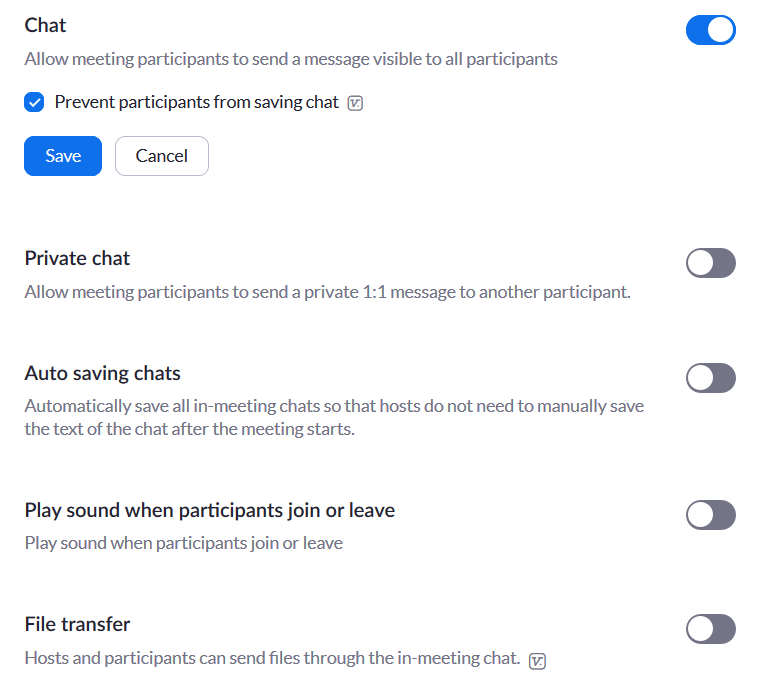
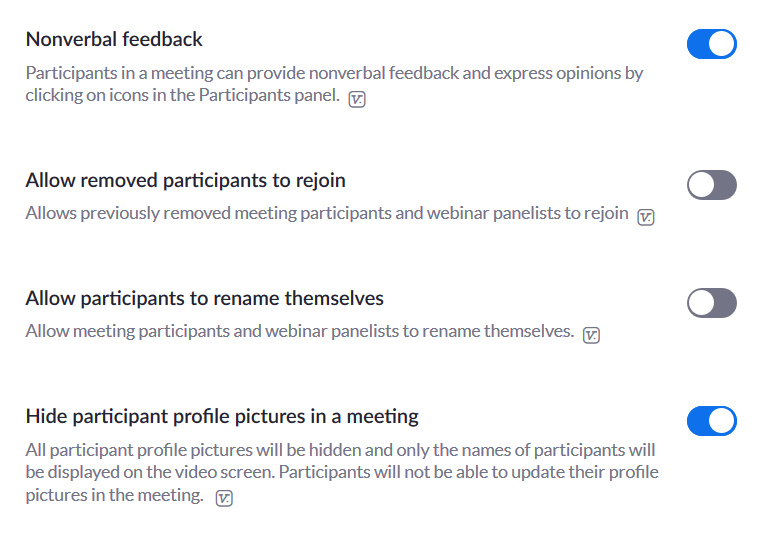
Disable private chat & File transfer
Disable private chat between participants to avoid distractions. Enable file transfer only if required.
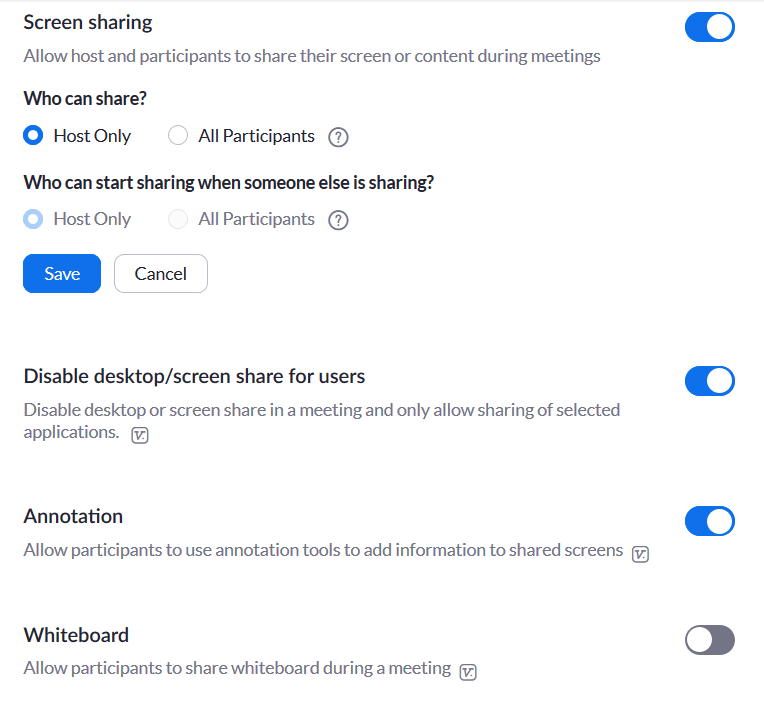
Control screen sharing
Screen sharing should only be controlled by the host and not the participants. Enable whiteboard in official meetings only if required.
Do not allow participants to rejoin meetings
Try not to let the participants who left the meeting rejoin, as you will have to authenticate the same users over and over throughout the meeting. Likewise, it’s better if all the interactions are non-verbal as verbal inputs can often get out of context.
Disable participants controlling features of the host
Don’t let the participants control any of the features that are meant to be used by the host.
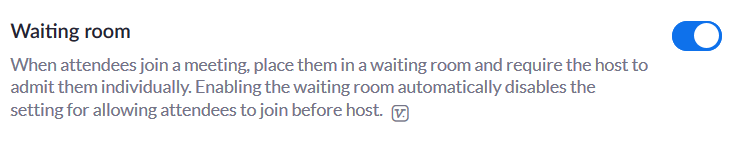
Participants in the Waiting room
Let the interested candidates be held up in a waiting room until the host authenticates them.
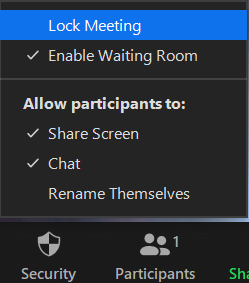
Lock participants until meeting complete
Lock the participants after a few minutes of commencement of the meeting to avoid participants joining and leaving the meeting repeatedly. Click on the security option on the bottom tab and select a lock meeting.
Update your Zoom App regularly
If you are using the Zoom app, the first thing to do is to check for updates and make sure you have the updated version of the app.
Set strong passwords
The meetings section of the Zoom app lets you change most of the above-mentioned settings quickly. Setting a strong and unpredictable password gives you better security than using randomly generated passwords. But remember to change this password for every meeting.
Uncheck Use of Personal meeting ID
Also, don’t forget to uncheck the Use my Personal Meeting ID option.
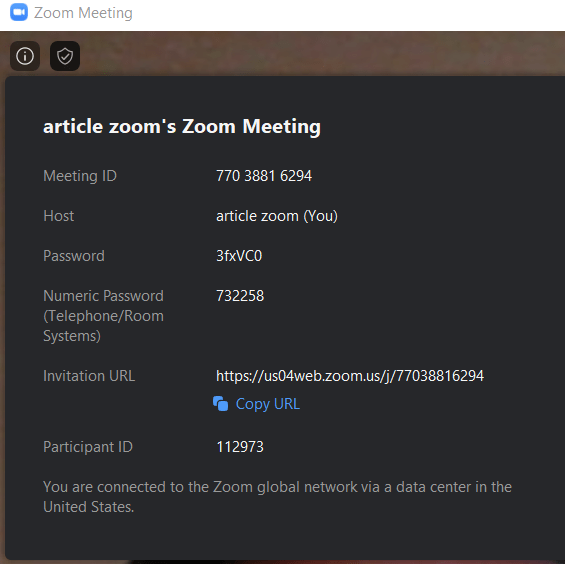
View your meeting details
Click on the info icon on the top right corner to view your meeting details which include the URL, randomly generated ID, and password.
A few more tips for you:
- Avoid sharing your meeting links on public platforms. Instead, share the randomly generated ID and password.
- If you are hosting a meeting, you must “end” the meeting, not “leave” the meeting.
- Strictly avoid sharing private and confidential information.
- Sign out of your account when not in use.
- In case you are using the paid version, create a webinar instead of a meeting. It has much lesser chances of getting hacked.
- A paid account also gives you the choice we told you about earlier, to select or opt-out of data centers through which your data is routed.
This move by zoom communicates out loud that it cares for the new user base it has gained in such a short time and that they are trying to ensure the safety of their users’ data. With these tweaks made, you’re one step closer to increasing your online privacy.
If you are interested in a completely more secure, more flexible and completely free video conferencing solution, then here it is Jitsi. You can build yourself massively scalable multiparty video conferencing solution.