To paraphrase Apple’s iPhone tagline, “If you don’t own a Mac … you don’t own a Mac ..!” It is as simple. And given the recent turn of events, Apple has, in the literal meaning, justified the above advert line.
In the past week, Apple has surreptitiously rolled out a security update to your OS X -run Macintosh to counter a particularly malicious flaw. This flaw was in the form of a serious security issue with the the Network Time Protocol (NTP), which has already proved to be quite dangerous in the past – as has been witnessed in the numerous successful Distributed Denial of Service (DDoS) attacks on various UNIX based machines : which even include the popular Linux and Mac OS X servers / machines.

Whilst, Apple initially recommended its Yosemite, Mountain Lion and Mavericks users to update their systems “as soon as possible”, it soon deemed it dangerous enough to ended up taking matters in its own hands and rolling out the security update via XProtect. In fact, Apple’s XProtect is so smooth that it even installs the update without requiring a reboot from any user – the only catch being you must have enabled your Mac to “install system data files and security updates” automatically (allowed by default).
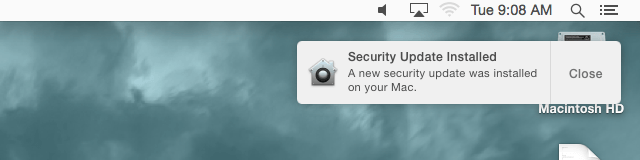
You can verify whether your Mac has received this update by enacting the following steps –
- Open the Terminal app in your Utilities folder
- Enter inwhat /usr/sbin/ntpd in the Terminal.
Apple states that you should view ntp-77.1.1 on Mountain Lion, ntp-88.1.1 on Mavericks, and ntp-92.5.1 on Yosemite. - If you see can view anything other than these version numbers, it is recommended that you perform a software update to ensure you are protected.

