My grandmother is often caught saying (often disdainfully), “Our kids turned out fine without computers”. And those of you, who just patted their backs, WAIT! Her kids mean our parents. And though I disagree with her on many levels, there’s just a trace of truth in her words. In this day and age, there are some (those who didn’t turn out fine) who can easily execute a crime without much contemplation, as they have technology in their pockets. It has become an indispensable part of our lives and the knowledge of this, gives a criminal mind an opening of sorts. The newest addition to this hall of shame is cybercrime. Though it has been around for a while now, off late new patterns and strategies are found in its execution. The target audience, the executer, everything has drastically changed. Their newest prey is the ATM machine.
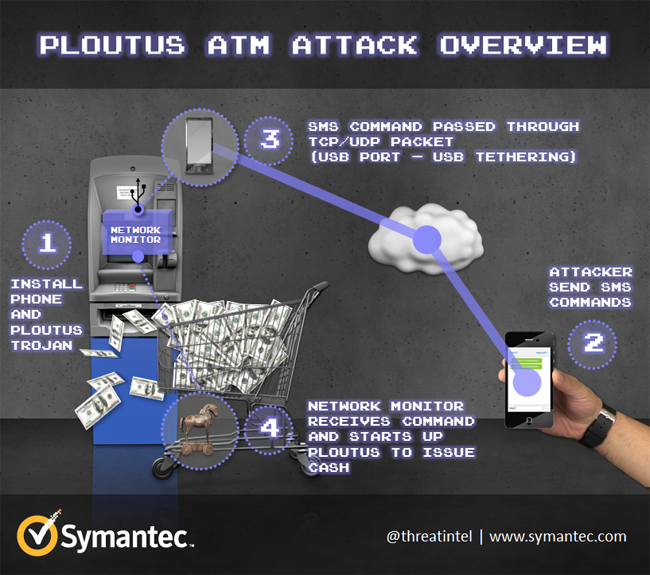
Not so long ago, a new malware named Backdoor.Ploutus was found in an ATM in Mexico. By using an external keyboard, these criminals could withdraw any desired amount. A week after discovering this malpractice, a new variant of Backdoor.Ploutus called Backdoor.Ploutus B was found and this time it was in English, indicating a franchise(or franchises) of the original one spreading across the globe. And interestingly, this time it was just a mere SMS which gave them the access to the bank’s customer’s cash.
Who are more susceptible to this crime?
As we all know, ATMs are computers that give us the access to our cash. It has been noticed that computers (i.e. ATMs) which run on Windows XP have been the main target of this type of crime. Surprisingly (and unfortunately) 95% banks have ATMs that run on Windows XP. And, with the announcement of its (Windows XPs) departure (on April 8, 2014), this type of crime has substantially increased.
How do they do it?
It seems easy, but a lot of brain muscles have been exercised in designing the Ploutus B. The mobile phone is connected to the ATM through the USB port (Yes that is possible!). Once the connection has been secured, the ATM is infected with the Ploutus. Then, the criminal feeds in specific message into the phone, detecting which the phone converts the message into a network packet and forwards it to the ATM.
The Network Packet Monitor (NPM) is an entity of the malware which can detect the network traffic in an ATM. The process then begins! The ATM on coming across a valid UDP or TCP packet accepts the command and spews out cash. After detecting and accepting the first UDP, the ATM moves on to detect the next. The command looks something like the following-
cmd.exe /c PLOUTOS.EXE 5449610000583686=2836957412536985
Are there others of the sort?
Actually, there are! Symantec Security Response has found other malwares apart from Ploutus infecting the ATMs. While Ploutus steal money from inside the ATM, there are malware which tries to steal the customer’s banking credentials and PIN code as well. And if nothing works, threatening the customer is always an option.
How can ATMs and customers be protected?
Nothing is ever full-proof, not even security. But precaution always comes in handy. Following are few of them-
- Upgrading the ATMs to Windows7 or Windows8
- Tightening up security and setting up a fully functioning CCTV.
- To ward off disk tampering, full disk encryption should be used
- To prevent booting from unauthorised media like CD ROMs and USB sticks, the BIOS should be locked down.
- And a system lock down solution should be definitely used.
- Hope and pray you are not victimised (and others as well).


