If you turn on your computer and are greeted to a message telling you that your business is at risk, and your files are encrypted, and you’re asked to pay for them to be decrypted, Then yes, you’ve fallen prey to yet another cyber attack. This time – if you haven’t already figured out – it’s an RYUK Ransomware. In case this isn’t the day all your files are suspiciously encrypted, then thank your antivirus program (and yourself for not being gullible enough to download ransomware infected files) and if you don’t have an antivirus, get one ASAP.
A high-risk ransomware virus going by the name RYUK has resurfaced again, after making rounds targeting business organizations for ransom in 2018, this time with an upgrade. It uses WoL (Wake on LAN) and then gains access to every computer on the network, further proceeding to infect them.
Ransomware is a virus that infects your computer by encrypting most of your data and then shows you a message, a demand for ransom that they ask you to pay, (usually in BitCoin (BTC) to ensure their privacy) in order to give you the keys to decrypt your data.
How does your PC get Infected?
Ransomware developers make use of other viruses like trojans, or spam/phishing emails, corrupted torrents, fake software updates and what not to spread ransomware. Spam emails contain attachments that are viruses, trojans download ransomware in the background and run it, sometimes fake software updates or seemingly legit “free downloads” of paid applications bring in malware like ransomware to your computer.
RYUK Ransomware upon infection does the following actions:
- Encrypts some or all of your files.
- The encrypted files have no file extension.
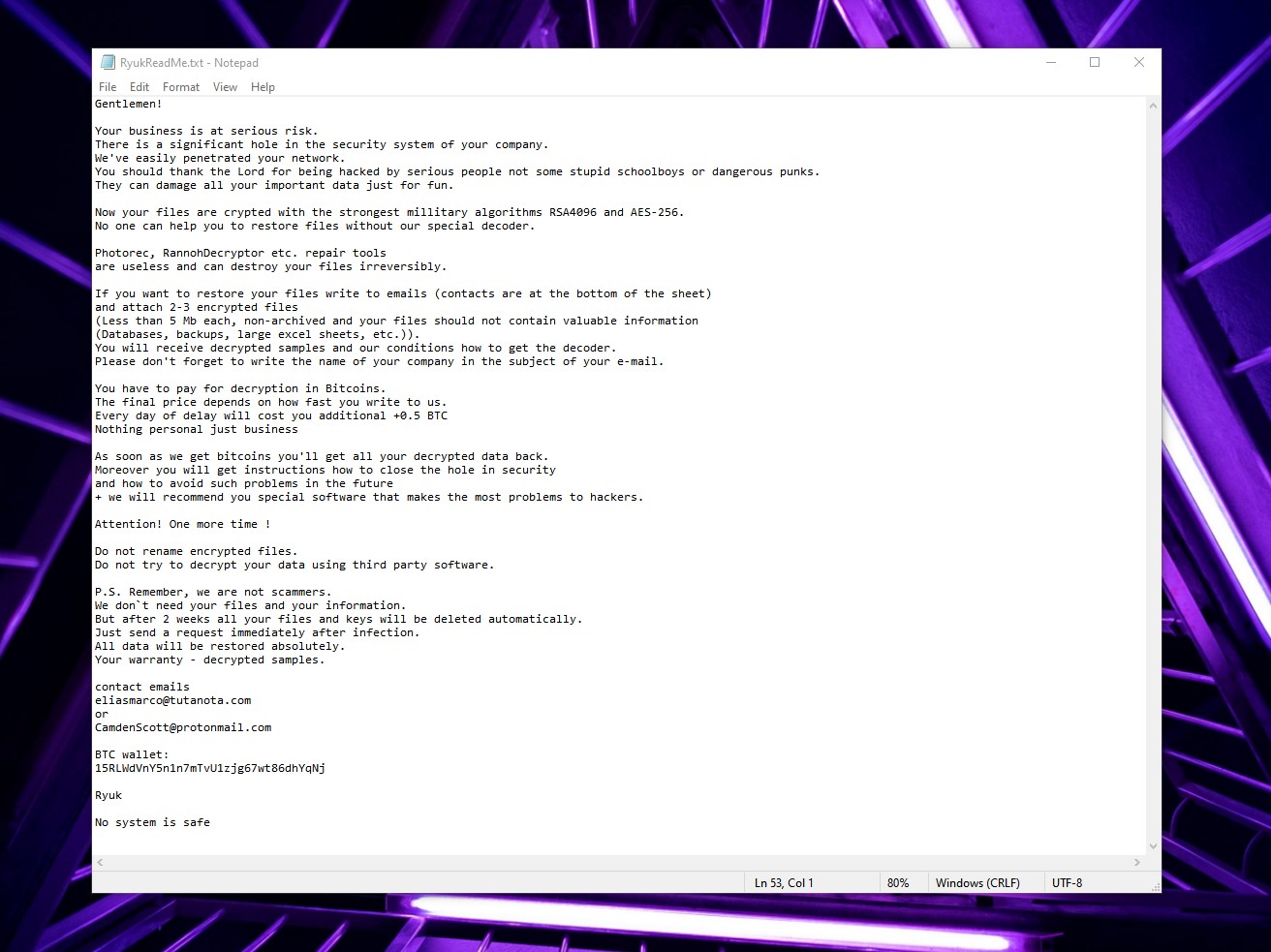
- Creates a text file named
RyukReadMe.txtin every folder whose contents are encrypted.- The text file contains the request for ransom, in BTC and also the encryption keys unique to each user.
- RYUK uses military-grade RSA-4096 and AED-265 encryption algorithms, so it is impossible to restore your data without these keys.
- The ransom amount is also a hefty price, going up to 0.5 BTC. However, given the targets of ransomware developers are large organizations, they just end up paying the amount.
- It isn’t guaranteed that they will provide you with the private keys once you pay the ransom, most of them ignore the victims after payment!
- It is impossible to decrypt these files without the keys and users are not encouraged to pay ransom either.
But as of late, RYUK developers have updated the virus. It is now equipped with the Wake-on-Lan feature to turn on power off devices on a compromised network to have greater success encrypting them.
Wake on LAN is a feature that administrators can use to turn on or wake up devices on a network from a switched off or sleep state. They can also use the same to mass deliver system updates to the devices on the network. RYUK exploits this to spread the ransomware to all the available devices on the network.
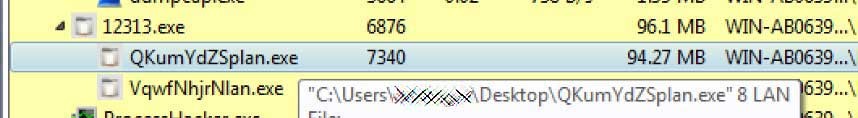
When the ransomware is executed, it will spawn multiple subprocesses with the argument 8 LAN.
These subprocesses scan the ARP table (Address Resolution table) of the device for IP addresses of other devices on the local network. The ARP table contains the list of IP addresses of devices on the network and the MAC addresses that are obtained when the ARP resolves the IP into its associated MAC address. It will then send the Wake on LAN request to these devices using their MAC addresses and wakes them up.
If the request was successful and the device is woken up, Ryuk will encrypt that remote computer’s drive as well.
This poses a threat to most organizations as they have all devices on a network, and the network is usually overseen by an administrator. WoL exploitation creates a large reach as just one infected PC might mean the compromisation of the entire network in large corporate environments.
The process does not do any harm to Linux based computers, but still, the looming threat persists because the ransomware can definitely gain access to the devices, and just cannot encrypt them.
How to stay safe from RYUK Ransomware attack?
Preventive measures are the only possible way to stay safe from such attacks, however, there are very few modes of repair.
- Administrators should only allow Wake-on-Lan packets from administrative devices and workstations. However, this doesn’t help much once the administrator device is compromised.
- Using a reputed antivirus program.
- Staying safe while downloading files from torrents.
- Obtain all your software from trusted and original sources.
- It is preferred to make a switch to Linux based computers.
- Maintaining frequent system backups. The only trustworthy and reliable way to get back your files once RYUK hits you is to perform a system restore, so having strategically planned restore points as often as possible help.
It is also advised to keep regular backups in physical media that is not connected to your network. You can find the complete details of RYUK Ransomware here.